If you are searching about PKI Service for Large Scale IPSec Aggregation - Cisco you've visit to the right page. We have 17 Images about PKI Service for Large Scale IPSec Aggregation - Cisco like Customer PKI Root Diagrams - Connectors2 Overview - HydrantID, How PKI Works and also Scott Rea - IoT: Taking PKI Where No PKI Has Gone Before. Here you go:
PKI Service For Large Scale IPSec Aggregation - Cisco
pki key obtaining ipsec cisco security aggregation scale service follows stages illustrated general figure
A Microsoft PKI Quick Guide – Part 3: Installation
pki microsoft quick guide installation each validity period practice level figure
What Is SSL And What Is The Use Of SSL Certificates? | Proxiesforent
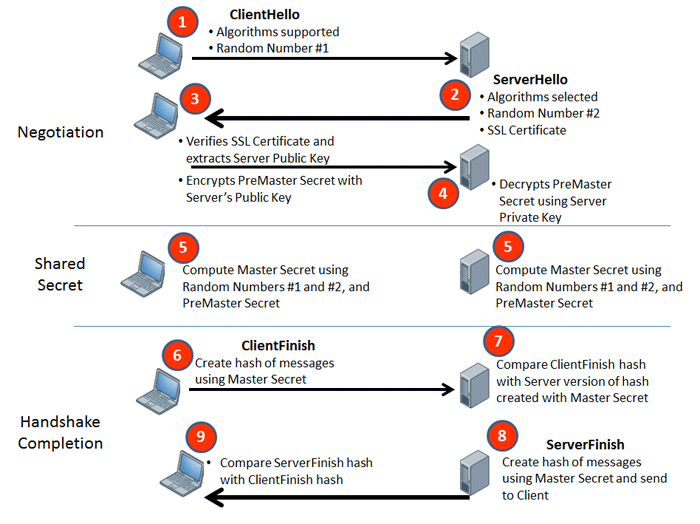 proxiesforent.com
proxiesforent.com diagram certificates process does step certificate key secret master pre interpretation correct pair client
PKA Key Management
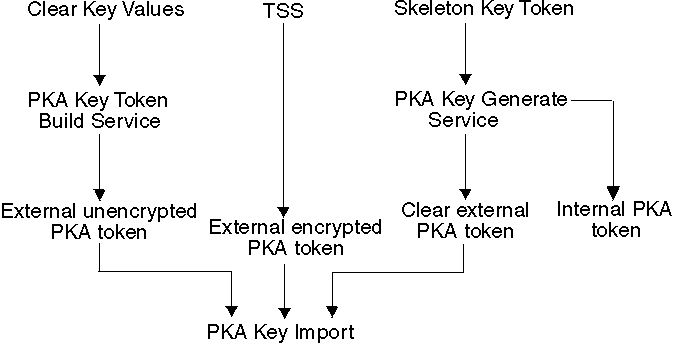 www.ibm.com
www.ibm.com pka ibm
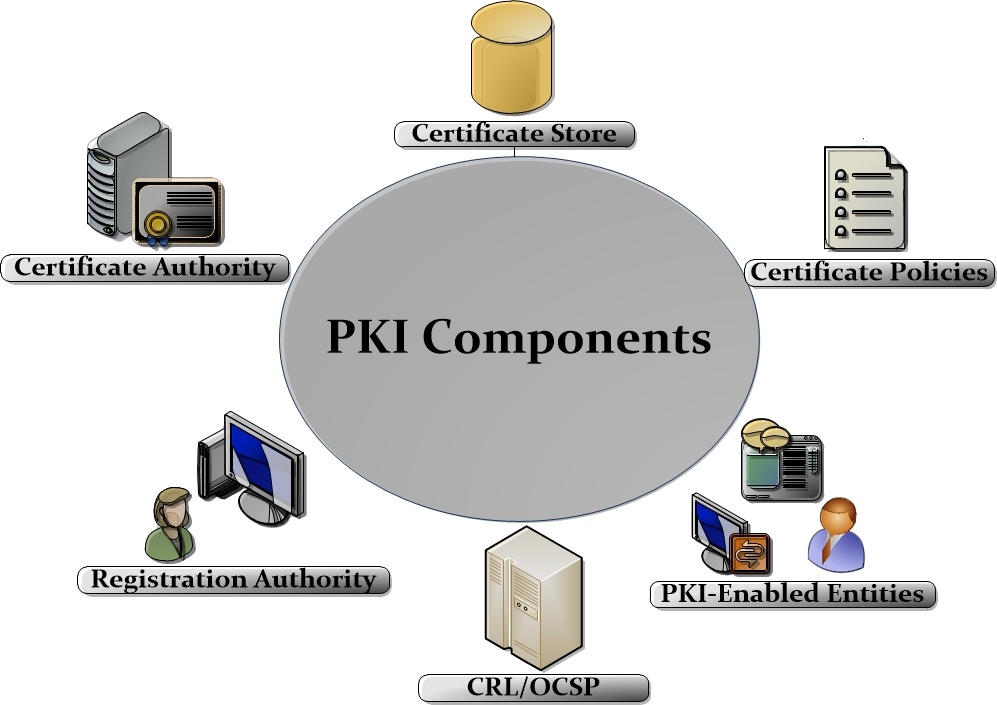
What Is PKI?
 www.entrust.com
www.entrust.com pki entrust
How PKI Works
 godinus123.blogspot.com
godinus123.blogspot.com pki sake
HTTPS Communication Data Encryption
communication encryption data pki
User Authentication Workflows — QGIS Documentation Documentation
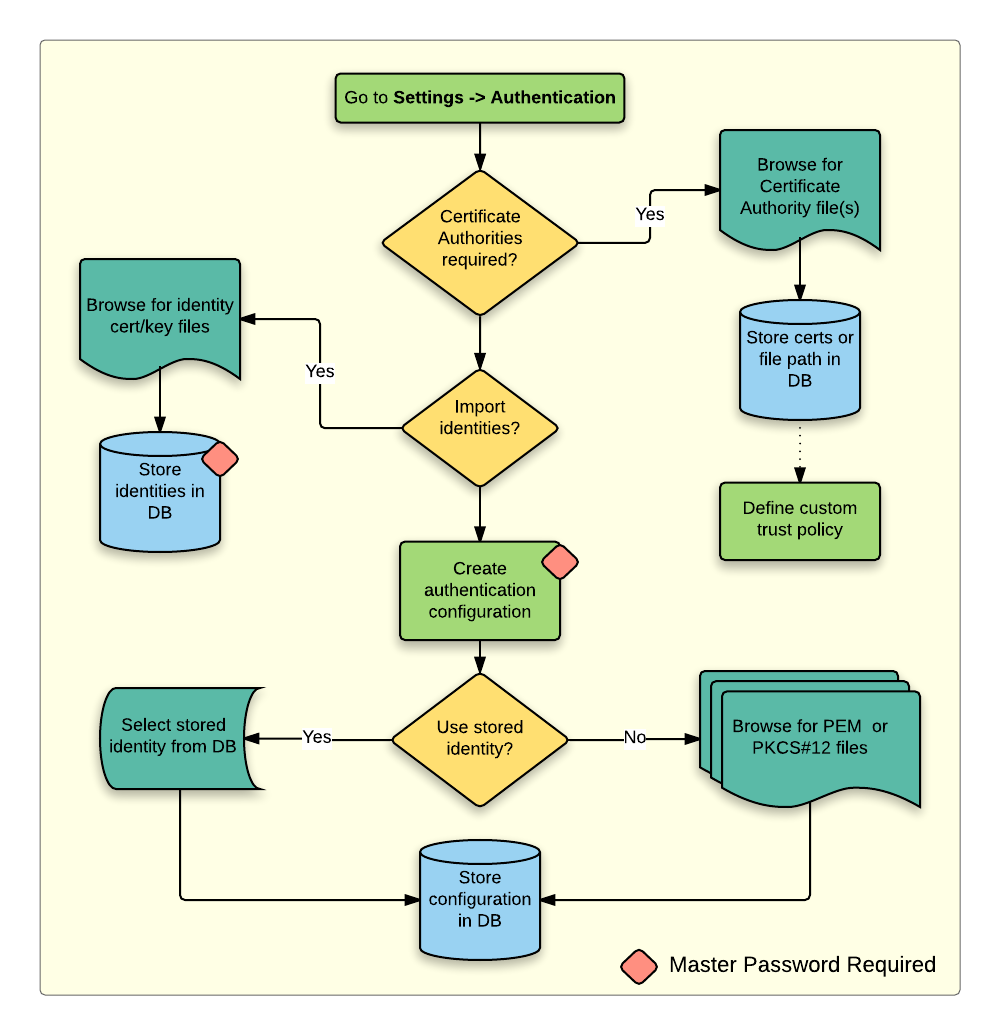 docs.qgis.org
docs.qgis.org pki workflow workflows configuration user qgis auth authentication
PKI | Networking
 efagundes.com
efagundes.com pki
9.3. Public Key Cryptography
digital signature key signatures cryptography integrity gt4 globus tutorial figure security concepts lbs huihoo docs
McSeven – Primus Esse Delectat » Blog Archive » Papier: Sichere EMail
Scott Rea - IoT: Taking PKI Where No PKI Has Gone Before
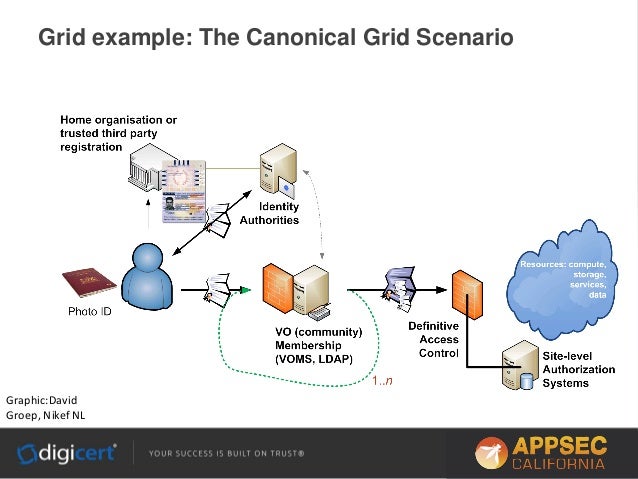 www.slideshare.net
www.slideshare.net pki rea
PKI Service For Large Scale IPSec Aggregation - Cisco
 www.cisco.com
www.cisco.com ipsec pki ike cisco protocol aggregation scale service certificates
PKI - PKI - JapaneseClass.jp
 japaneseclass.jp
japaneseclass.jp pki emv
High-level Example Of Hub And Spoke VDC | Networking, Cloud
 www.pinterest.com
www.pinterest.com datacenter vdc routing level topologia region voorbeeld spokes implementation gwiazdy netzwerktopologie sql
Customer PKI Root Diagrams - Connectors2 Overview - HydrantID
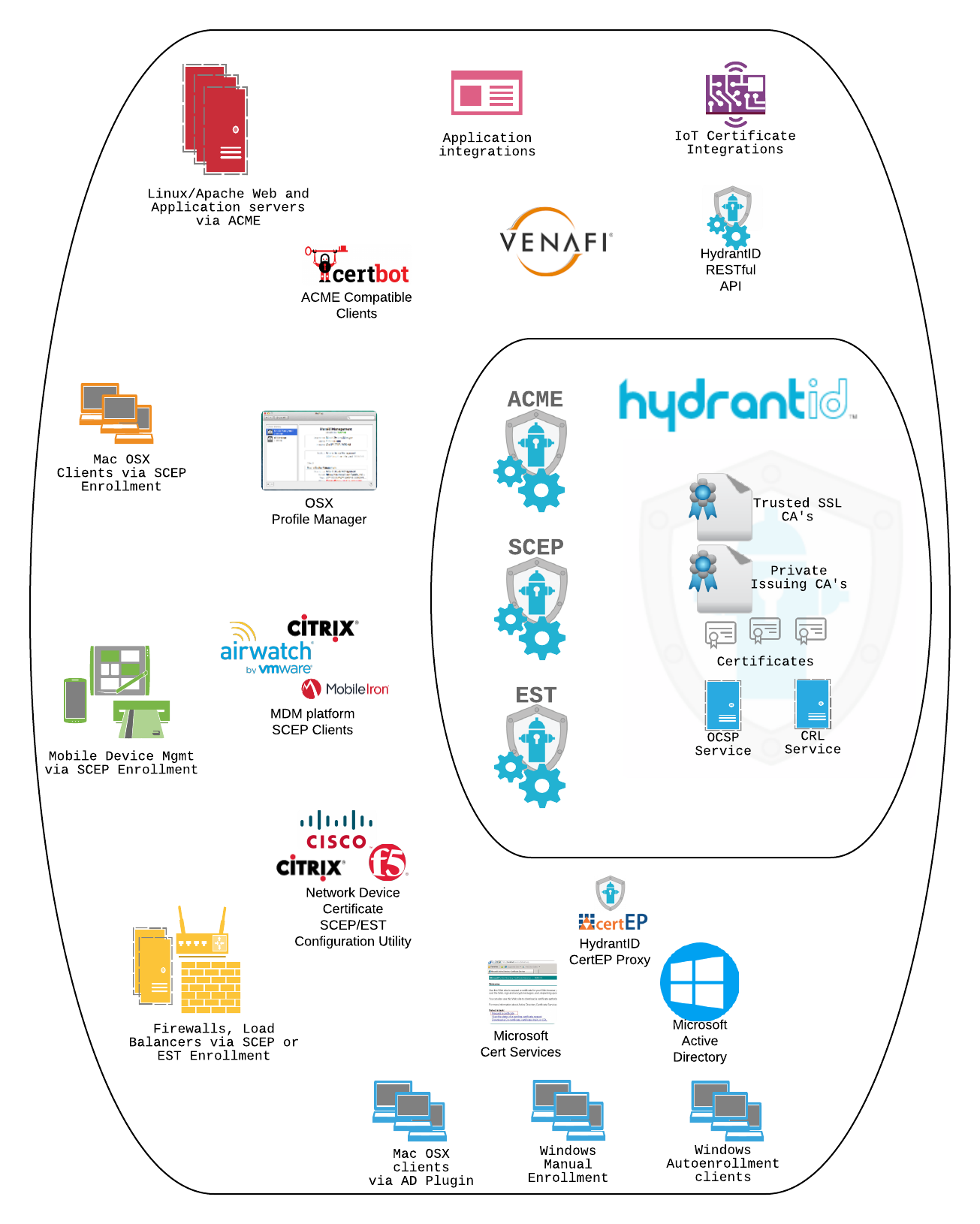 hydrantid.com
hydrantid.com pki diagrams root overview customer
How PKI Works Towards Securing Your Organization?
 www.cheapsslshop.com
www.cheapsslshop.com pki securing
Customer pki root diagrams. A microsoft pki quick guide – part 3: installation. 9.3. public key cryptography
if you are looking "id":96,"keyword_id":2,"name":"PKI Diagram","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1462,"keyword_id":96,"url":"https:\/\/hydrantid.com\/wp-content\/uploads\/2018\/03\/Customer-PKI-Root-Diagrams-Connectors2-Overview.png","link":"https:\/\/hydrantid.com\/solutions\/attachment\/customer-pki-root-diagrams-connectors2-overview\/","title":"Customer PKI Root Diagrams - Connectors2 Overview - HydrantID","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.kl2zwuC7xioLNEmHka0cWgHaJQ&pid=15.1","size":"1305 x 1630 \u00b7 png","desc":"pki diagrams root overview customer","filetype":"png","width":1305,"height":1630,"domain":"hydrantid.com","created_at":null,"updated_at":null,"id":1463,"keyword_id":96,"url":"https:\/\/4.bp.blogspot.com\/-pofx1OtKB0Q\/W7gk50XTQhI\/AAAAAAAGS1Q\/x2KfFHW4Bm06yZxuHoNM6DhBSbTZZcY8gCLcBGAs\/s1600\/PKI.png","link":"http:\/\/godinus123.blogspot.com\/2018\/10\/active-directory-how-pki-works-may-13.html","title":"How PKI Works","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.jqPNnuOHs7rVWLfd31UG5gHaDt&pid=15.1","size":"759 x 381 \u00b7 png","desc":"pki sake","filetype":"png","width":759,"height":381,"domain":"godinus123.blogspot.com","created_at":null,"updated_at":null,"id":1464,"keyword_id":96,"url":"https:\/\/www.cheapsslshop.com\/blog\/wp-content\/uploads\/2020\/10\/Picture1.png","link":"https:\/\/www.cheapsslshop.com\/blog\/how-pki-works-towards-securing-your-organization\/","title":"How PKI Works towards securing your organization?","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.d07oj9vWWUiGWwCxT4vO8gHaDE&pid=15.1","size":"486 x 201 \u00b7 png","desc":"pki securing","filetype":"png","width":486,"height":201,"domain":"www.cheapsslshop.com","created_at":null,"updated_at":null,"id":1465,"keyword_id":96,"url":"https:\/\/www.cryptomathic.com\/hubfs\/Images_misc\/Blog-Photos\/PKI-Components.jpg","link":"https:\/\/japaneseclass.jp\/trends\/about\/PKI","title":"PKI - PKI - JapaneseClass.jp","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.tgcGepwUkOT8MHgYKgMSegHaFP&pid=15.1","size":"997 x 705 \u00b7 jpeg","desc":"pki emv","filetype":"jpg","width":997,"height":705,"domain":"japaneseclass.jp","created_at":null,"updated_at":null,"id":1466,"keyword_id":96,"url":"https:\/\/docs.qgis.org\/3.4\/en\/_images\/auth-pki-config.png","link":"https:\/\/docs.qgis.org\/3.4\/en\/docs\/user_manual\/auth_system\/auth_workflows.html","title":"User Authentication Workflows \u2014 QGIS Documentation documentation","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.iViNcgUh1d9hEGfRFe9PLwHaHq&pid=15.1","size":"1000 x 1035 \u00b7 png","desc":"pki workflow workflows configuration user qgis auth authentication","filetype":"png","width":1000,"height":1035,"domain":"docs.qgis.org","created_at":null,"updated_at":null,"id":1467,"keyword_id":96,"url":"http:\/\/www.windowsecurity.com\/img\/upl\/image0021187011381011.jpg","link":"http:\/\/www.windowsecurity.com\/articles-tutorials\/authentication_and_encryption\/Microsoft-PKI-Quick-Guide-Part3.html","title":"A Microsoft PKI Quick Guide \u2013 Part 3: Installation","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.M8FGWoFlHRqYiO8hQWx4YwHaD-&pid=15.1","size":"571 x 307 \u00b7 jpeg","desc":"pki microsoft quick guide installation each validity period practice level figure","filetype":"jpg","width":571,"height":307,"domain":"www.windowsecurity.com","created_at":null,"updated_at":null,"id":1468,"keyword_id":96,"url":"https:\/\/www.entrust.com\/-\/media\/entrust\/resources\/product-support\/certificate-solutions\/pkicomponents-300x201.gif?la=en&hash=D96A370EB84561D313405202BAED6392","link":"https:\/\/www.entrust.com\/resources\/certificate-solutions\/learn\/what-is-pki","title":"What is PKI?","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.CGARmHN3GEAA5CJxiSLlUAHaE9&pid=15.1","size":"300 x 201 \u00b7 gif","desc":"pki entrust","filetype":"gif","width":300,"height":201,"domain":"www.entrust.com","created_at":null,"updated_at":null,"id":1469,"keyword_id":96,"url":"http:\/\/www.herongyang.com\/PKI\/HTTPS_Communication_Encryption.jpg","link":"http:\/\/www.herongyang.com\/PKI\/HTTPS-Communication-Data-Encryption.html","title":"HTTPS Communication Data Encryption","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.5zJlXkZSm1KrwlX8UHSw5wHaDn&pid=15.1","size":"485 x 237 \u00b7 jpeg","desc":"communication encryption data pki","filetype":"jpg","width":485,"height":237,"domain":"www.herongyang.com","created_at":null,"updated_at":null,"id":1470,"keyword_id":96,"url":"http:\/\/www.cisco.com\/c\/dam\/en\/us\/td\/i\/200001-300000\/220001-230000\/226001-227000\/226762.eps\/_jcr_content\/renditions\/226762.jpg","link":"http:\/\/www.cisco.com\/c\/en\/us\/td\/docs\/solutions\/Enterprise\/Security\/PKI-security.html","title":"PKI Service for Large Scale IPSec Aggregation - Cisco","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.fJALSjmAwHkKkdMw6Kh28QHaDA&pid=15.1","size":"546 x 222 \u00b7 jpeg","desc":"pki key obtaining ipsec cisco security aggregation scale service follows stages illustrated general figure","filetype":"jpg","width":546,"height":222,"domain":"www.cisco.com","created_at":null,"updated_at":null,"id":1471,"keyword_id":96,"url":"https:\/\/www.cisco.com\/c\/dam\/en\/us\/td\/i\/200001-300000\/220001-230000\/226001-227000\/226761.eps\/_jcr_content\/renditions\/226761.jpg","link":"https:\/\/www.cisco.com\/c\/en\/us\/td\/docs\/solutions\/Enterprise\/Security\/PKI-security.html","title":"PKI Service for Large Scale IPSec Aggregation - Cisco","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.S4tlTgfzCVBao5mbtqz1yQAAAA&pid=15.1","size":"381 x 205 \u00b7 jpeg","desc":"ipsec pki ike cisco protocol aggregation scale service certificates","filetype":"jpg","width":381,"height":205,"domain":"www.cisco.com","created_at":null,"updated_at":null,"id":1472,"keyword_id":96,"url":"https:\/\/efagundes.com\/networking\/wp-content\/uploads\/sites\/5\/2012\/11\/Slide279.png","link":"https:\/\/efagundes.com\/networking\/seguranca-de-redes\/pki\/","title":"PKI ,"id":1473,"keyword_id":96,"url":"https:\/\/proxiesforent.com\/blog\/wp-content\/uploads\/2015\/07\/learn_ssl_diagram.gif","link":"https:\/\/proxiesforent.com\/blog\/2015\/07\/11\/what-is-ssl-and-what-is-the-use-of-ssl-certificates\/","title":"What is SSL and what is the use of SSL certificates? ,"id":1474,"keyword_id":96,"url":"http:\/\/docs.huihoo.com\/globus\/gt4-tutorial\/images\/security_concepts_digitalsig.png","link":"http:\/\/docs.huihoo.com\/globus\/gt4-tutorial\/ch09s03.html","title":"9.3. Public key cryptography","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.lNQb_FRf9zfvDnNOGpp-9wHaFN&pid=15.1","size":"650 x 457 \u00b7 png","desc":"digital signature key signatures cryptography integrity gt4 globus tutorial figure security concepts lbs huihoo docs","filetype":"png","width":650,"height":457,"domain":"docs.huihoo.com","created_at":null,"updated_at":null,"id":1475,"keyword_id":96,"url":"http:\/\/www.mcseven.me\/wp-content\/uploads\/2009\/05\/rsa_encryption.png","link":"http:\/\/www.mcseven.me\/2009\/05\/papier-sichere-email-fur-webanwendungen\/","title":"McSeven \u2013 primus esse delectat \u00bb Blog Archive \u00bb Papier: Sichere eMail","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.0XkVVvxHBkkx3o0pB_6e-wHaHP&pid=15.1","size":"525 x 513 \u00b7 png","desc":"","filetype":"png","width":525,"height":513,"domain":"www.mcseven.me","created_at":null,"updated_at":null, Networking, Cloud","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.OWTdk7412OWZw6MqNdCAuQHaGN&pid=15.1","size":"722 x 605 \u00b7 png","desc":"datacenter vdc routing level topologia region voorbeeld spokes implementation gwiazdy netzwerktopologie sql","filetype":"png","width":722,"height":605,"domain":"www.pinterest.com","created_at":null,"updated_at":null,"id":1477,"keyword_id":96,"url":"https:\/\/www.ibm.com\/support\/knowledgecenter\/en\/SSLTBW_2.1.0\/com.ibm.zos.v2r1.csfb400\/csfb4012.gif","link":"https:\/\/www.ibm.com\/support\/knowledgecenter\/en\/SSLTBW_2.1.0\/com.ibm.zos.v2r1.csfb400\/pkaman.htm","title":"PKA Key Management","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.N0ZTR1C1l1riRx8iG1r6DQHaDx&pid=15.1","size":"673 x 343 \u00b7 gif","desc":"pka ibm","filetype":"gif","width":673,"height":343,"domain":"www.ibm.com","created_at":null,"updated_at":null,"id":1478,"keyword_id":96,"url":"https:\/\/image.slidesharecdn.com\/lqqrjt43tnyuhwafpmuo-signature-be1526f88900615949404dd62c6eab38cea9ada23c285556875639b0cb3132d4-poli-150204113934-conversion-gate02\/95\/scott-rea-iot-taking-pki-where-no-pki-has-gone-before-45-638.jpg?cb=1423064129","link":"http:\/\/www.slideshare.net\/DigiCertCom\/app-sec2015","title":"Scott Rea - IoT: Taking PKI Where No PKI Has Gone Before","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.bK4q7PoraTP68xK8TKNyJQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki rea","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Diagram Pki service for large scale ipsec aggregation. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment