If you are looking for Basic concept of pki you've visit to the right web. We have 14 Images about Basic concept of pki like PKI for EMV cards compliant to PCI DSS, The new rocket science stuff in microsoft pki and also CyberArk Enterprise Vault - The only Enterprise Vault tutorial you need. Read more:
Basic Concept Of Pki
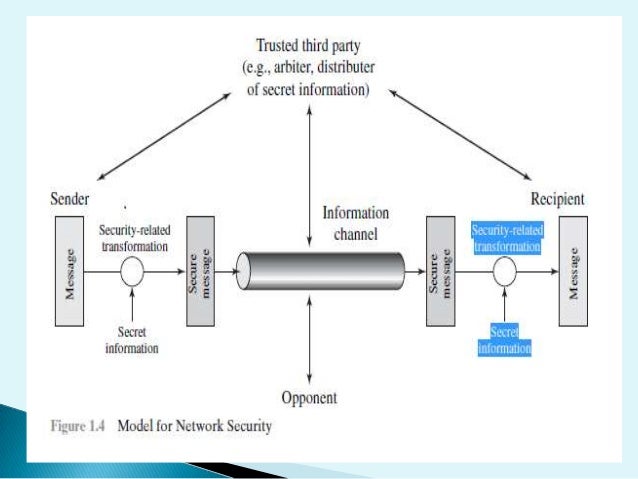 www.slideshare.net
www.slideshare.net pki
The New Rocket Science Stuff In Microsoft Pki
 www.slideshare.net
www.slideshare.net pki
Windows Secure Boot Key Creation And Management Guidance | Microsoft Docs
 docs.microsoft.com
docs.microsoft.com windows boot secure key architecture management platform hardware trusted microsoft desktop guidance creation docs secureboot os
CyberArk Enterprise Vault - The Only Enterprise Vault Tutorial You Need
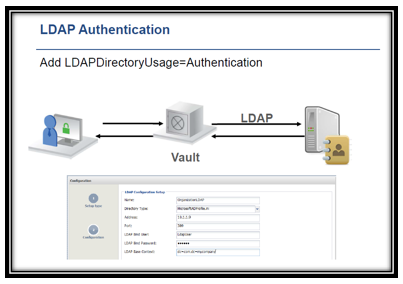 cloudfoundation.com
cloudfoundation.com cyberark vault tutorial enterprise authentication ldap ad etc radius need protocol novell rsa certificate ones uses external directory secure sun
How PKI Works ? - RebelAdmin.com
pki works process rebeladmin
Cyber Security Accountability: Who In The C-Suite Should Care? | Venafi
 www.venafi.com
www.venafi.com security care accountability venafi suite should encrypted attacks itself turned
Review – “The Seven Properties Of Highly Secure Devices” From Microsoft
 iotgossiper.com
iotgossiper.com pki certificate highly secure properties process deployment models devices microsoft seven rebeladmin hierarchy directory active standalone certificates cas created
Why Integrate Machine Identity Protection With CAs | Venafi
 www.venafi.com
www.venafi.com why identity protection machine venafi integrate authorities certificate should
Online Digital Privacy & The Crypto Wars | Venafi
 www.venafi.com
www.venafi.com telegram privacy digital venafi war russia fight crypto wars casualty messaging app defender encryption assaults
PKI Framework For Supporting The Security Of Mobile Communication From
pki security framework certificate authentication system certification mobile infrastructure key authority certificates supporting communication core certs its infra trusted organizations
Pki Diagram
 bishosoft.com
bishosoft.com pki diagram
PKI For EMV Cards Compliant To PCI DSS
 www.cryptomathic.com
www.cryptomathic.com pki emv
Summary Of Protocols For PKI Interoperability
 www.entrust.com
www.entrust.com pki summary interoperability protocols component brief purpose each entrust
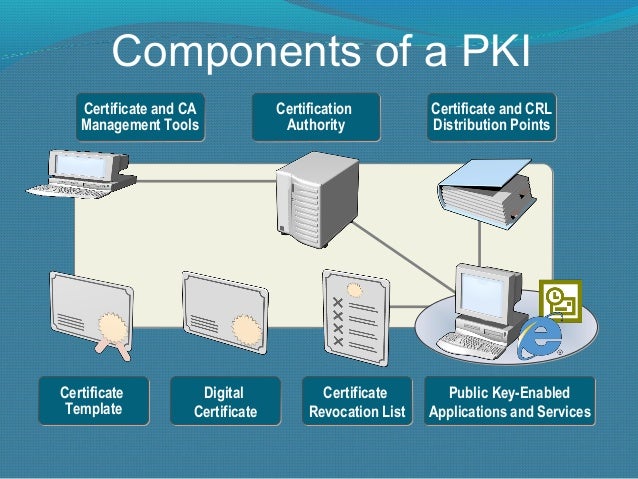
Overview Of Public Key Infrastructure, Certificate Management And
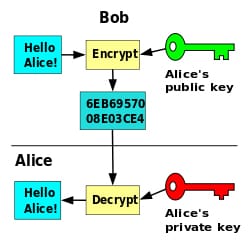 www.examcollection.com
www.examcollection.com key infrastructure components overview cryptography encryption keys associated certificate management wikipedia examcollection
Pki emv. Windows secure boot key creation and management guidance. Windows boot secure key architecture management platform hardware trusted microsoft desktop guidance creation docs secureboot os
if you are looking "id":108,"keyword_id":2,"name":"PKI Components","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1664,"keyword_id":108,"url":"https:\/\/www.cryptomathic.com\/hs-fs\/hubfs\/Images_misc\/Blog-Photos\/PKI-Components.jpg?width=1779&name=PKI-Components.jpg","link":"https:\/\/www.cryptomathic.com\/news-events\/blog\/pki-for-emv-cards-compliant-to-pci-dss","title":"PKI for EMV cards compliant to PCI DSS","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.tgcGepwUkOT8MHgYKgMSegHaFP&pid=15.1","size":"997 x 705 \u00b7 jpeg","desc":"pki emv","filetype":"jpg","width":997,"height":705,"domain":"www.cryptomathic.com","created_at":null,"updated_at":null,"id":1665,"keyword_id":108,"url":"https:\/\/image.slidesharecdn.com\/thenewrocketsciencestuffinmicrosoftpki-100518155734-phpapp02\/95\/the-new-rocket-science-stuff-in-microsoft-pki-8-638.jpg?cb=1422657832","link":"https:\/\/www.slideshare.net\/nathanwinters\/the-new-rocket-science-stuff-in-microsoft-pki-4142408","title":"The new rocket science stuff in microsoft pki","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.m7F9EvuQYIONKAe4FlxEnwHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1666,"keyword_id":108,"url":"http:\/\/tweenpath.net\/wp-content\/uploads\/PKI.gif","link":"https:\/\/tweenpath.net\/pki-framework-for-supporting-the-security-of-mobile-communication-from-its-core\/","title":"PKI Framework for Supporting the Security of Mobile Communication from","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.Ph1gyTl8JUF_WrqVzvsRuQHaGv&pid=15.1","size":"500 x 455 \u00b7 gif","desc":"pki security framework certificate authentication system certification mobile infrastructure key authority certificates supporting communication core certs its infra trusted organizations","filetype":"gif","width":500,"height":455,"domain":"tweenpath.net","created_at":null,"updated_at":null,"id":1667,"keyword_id":108,"url":"https:\/\/www.entrust.com\/-\/media\/entrust\/resources\/product-support\/certificate-solutions\/managedpki.gif?la=en&hash=2162166F1AE7DDF23B5BF6CDFDAB7B6C","link":"https:\/\/www.entrust.com\/resources\/certificate-solutions\/learn\/summary-of-protocols-for-pki-interoperability","title":"Summary of Protocols for PKI Interoperability","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.ny2hOu37ohdTioUq2S18bQAAAA&pid=15.1","size":"418 x 246 \u00b7 gif","desc":"pki summary interoperability protocols component brief purpose each entrust","filetype":"gif","width":418,"height":246,"domain":"www.entrust.com","created_at":null,"updated_at":null,"id":1668,"keyword_id":108,"url":"http:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/pki6.png","link":"http:\/\/www.rebeladmin.com\/2018\/05\/how-pki-works\/","title":"How PKI Works ? - RebelAdmin.com","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.O0rojEYpa8moff6jtAx-EgHaDc&pid=15.1","size":"924 x 429 \u00b7 png","desc":"pki works process rebeladmin","filetype":"png","width":924,"height":429,"domain":"www.rebeladmin.com","created_at":null,"updated_at":null,"id":1669,"keyword_id":108,"url":"http:\/\/bp0.blogger.com\/_2xduua7nmyw\/SIUoRSXs5bI\/AAAAAAAAAQg\/C49rqGDuoro\/s400\/Figure%2B2%2B-%2BStandard%2BPKI%2BInfrastructure.jpg","link":"http:\/\/bishosoft.com\/js\/pki-diagram","title":"Pki Diagram","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.h_qT7QNndLn-lRfoigqCnwAAAA&pid=15.1","size":"400 x 325 \u00b7 jpeg","desc":"pki diagram","filetype":"jpg","width":400,"height":325,"domain":"bishosoft.com","created_at":null,"updated_at":null,"id":1670,"keyword_id":108,"url":"https:\/\/image.slidesharecdn.com\/basicconceptofpki-130426145529-phpapp01\/95\/basic-concept-of-pki-6-638.jpg?cb=1366988166","link":"https:\/\/www.slideshare.net\/PrabhatGoel1\/basic-concept-of-pki","title":"Basic concept of pki","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.DG5t_Eyz8X4u4mO7HKLZoQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1671,"keyword_id":108,"url":"https:\/\/i1.wp.com\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/ca3.png","link":"https:\/\/iotgossiper.com\/2019\/09\/11\/review-the-seven-properties-of-highly-secure-devices-from-microsoft\/","title":"Review \u2013 \u201cThe Seven Properties of Highly Secure Devices\u201d from Microsoft","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.Q0wQp2L-_-OoNaDcZDlj7gHaF2&pid=15.1","size":"604 x 477 \u00b7 png","desc":"pki certificate highly secure properties process deployment models devices microsoft seven rebeladmin hierarchy directory active standalone certificates cas created","filetype":"png","width":604,"height":477,"domain":"iotgossiper.com","created_at":null,"updated_at":null,"id":1672,"keyword_id":108,"url":"https:\/\/www.examcollection.com\/design\/wikipic\/256.jpg","link":"https:\/\/www.examcollection.com\/certification-training\/security-plus-overview-of-public-key-infrastructure-certificate-management-and-associated-components.html","title":"Overview of Public Key Infrastructure, Certificate Management and","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.X0OSENHXrPxW9UOeVbOjawAAAA&pid=15.1","size":"250 x 244 \u00b7 jpeg","desc":"key infrastructure components overview cryptography encryption keys associated certificate management wikipedia examcollection","filetype":"jpg","width":250,"height":244,"domain":"www.examcollection.com","created_at":null,"updated_at":null,"id":1673,"keyword_id":108,"url":"https:\/\/docs.microsoft.com\/en-us\/windows-hardware\/manufacture\/desktop\/images\/dep-8-secureboot-platform-integrity-architecture.png","link":"https:\/\/docs.microsoft.com\/en-us\/windows-hardware\/manufacture\/desktop\/windows-secure-boot-key-creation-and-management-guidance","title":"Windows Secure Boot Key Creation and Management Guidance ,"id":1674,"keyword_id":108,"url":"https:\/\/cloudfoundation.com\/blog\/wp-content\/uploads\/2018\/10\/word-image-169.png","link":"https:\/\/cloudfoundation.com\/blog\/cyberark-enterprise-vault-presentation\/","title":"CyberArk Enterprise Vault - The only Enterprise Vault tutorial you need","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.wJC16weaZfmbZ5nuwlyn4AAAAA&pid=15.1","size":"403 x 284 \u00b7 png","desc":"cyberark vault tutorial enterprise authentication ldap ad etc radius need protocol novell rsa certificate ones uses external directory secure sun","filetype":"png","width":403,"height":284,"domain":"cloudfoundation.com","created_at":null,"updated_at":null,"id":1675,"keyword_id":108,"url":"https:\/\/www.venafi.com\/sites\/default\/files\/content\/blog\/2018-02\/blog-image-75_0.jpg","link":"https:\/\/www.venafi.com\/blog\/crypto-wars-fight-be-defender-your-digital-privacy","title":"Online Digital Privacy & The Crypto Wars , Venafi","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.rXZWTQoOeXBbYopdbilSbQHaCA&pid=15.1","size":"1200 x 325 \u00b7 jpeg","desc":"security care accountability venafi suite should encrypted attacks itself turned","filetype":"jpg","width":1200,"height":325,"domain":"www.venafi.com","created_at":null,"updated_at":null,"id":1677,"keyword_id":108,"url":"https:\/\/www.venafi.com\/sites\/default\/files\/content\/blog\/2019-01\/ca1.jpg","link":"https:\/\/www.venafi.com\/blog\/why-should-you-integrate-machine-identity-protection-your-certificate-authorities","title":"Why Integrate Machine Identity Protection with CAs ] this site you are coming to the right page. Contains many images about PKI Components Pki works process rebeladmin. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment