If you are looking for ESCRYPT passes TISAX certification with flying colors | ESCRYPT you've came to the right web. We have 16 Pics about ESCRYPT passes TISAX certification with flying colors | ESCRYPT like What is PKI, Understanding the Role of Certificate Authority in PKI and also D.N. AIDIT (Pemimpin Partai Komunis Indonesia) - Success = Dream x Work. Here you go:
ESCRYPT Passes TISAX Certification With Flying Colors | ESCRYPT
 www.escrypt.com
www.escrypt.com tisax escrypt kaizen 認証 合格
Overall Cryptography And Pki Introduction
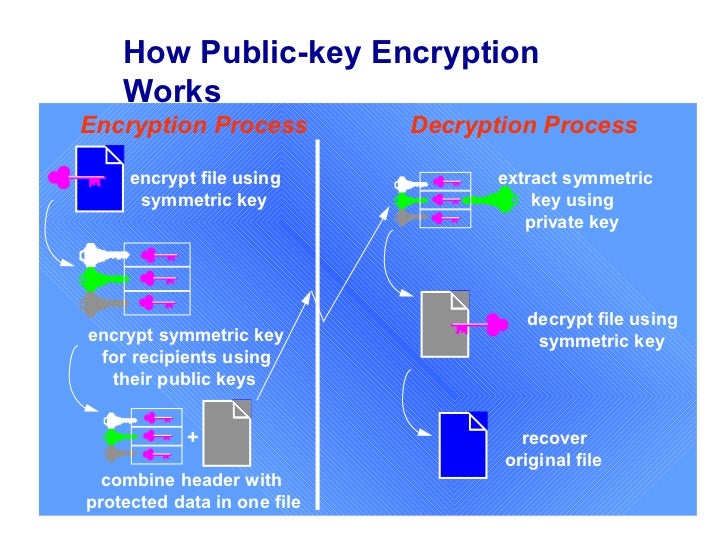 www.slideshare.net
www.slideshare.net pki cryptography encryption
The Internet Overview An Introduction To
 present5.com
present5.com introduction overview internet advertisements
What Is PKI
 software-engineer-tips-and-tricks.blogspot.com
software-engineer-tips-and-tricks.blogspot.com pki kerja 구성도 sertifikat certificado 사용 zertifikate atitude reflexiva
Understanding The Role Of Certificate Authority In PKI
 cheapsslsecurity.com
cheapsslsecurity.com pki infrastructure certification
Advanced PKI — OpenSSL PKI Tutorial
pki advanced tutorial root openssl pronged runs serve needs security readthedocs three its latest io
Welcome! - Challenge PKI Project
pki scheme federal very
Knowing The Modern PKI | PKI Fundamentals
 www.encryptionconsulting.com
www.encryptionconsulting.com pki
Addressing Key IoT Security Concerns For Manufacturers - IoT Now - How
iot security key concerns addressing manufacturers device identity strong
Learn Public Key Infrastructure (PKI) Basics - Part 1 - Codegic
 www.codegic.com
www.codegic.com pki
An Overview Of PKI | Mastering OpenVPN
 subscription.packtpub.com
subscription.packtpub.com pki
AUTOSAR Security: Achieving Integrated Cybersecurity With The Adaptive
 www.escrypt.com
www.escrypt.com autosar security adaptive achieving cybersecurity integrated platform
D.N. AIDIT (Pemimpin Partai Komunis Indonesia) - Success = Dream X Work
 beranimimpi.blogspot.com
beranimimpi.blogspot.com aidit pki komunis pahlawan revolusi jenazah partai misteri rossrightangle pemimpin nusantara terkuak candu agama aidat paham indocropcircles perintah supersemar maret
The Internet Overview An Introduction To
 present5.com
present5.com Support - 31-PKI Operation- H3C
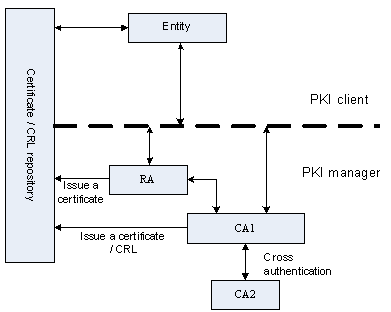 www.h3c.com
www.h3c.com pki h3c architecture figure configuration
Understanding Public Key Infrastructure: The Wide World Of PKI
 www.thesslstore.com
www.thesslstore.com pki wide key infrastructure hashed re trust
An overview of pki. Overall cryptography and pki introduction. Addressing key iot security concerns for manufacturers
if you are looking "id":79,"keyword_id":2,"name":"pki system","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1165,"keyword_id":79,"url":"https:\/\/2.bp.blogspot.com\/-_fWrkvGJ7iY\/UFrZPpFoXLI\/AAAAAAACk_4\/pV2EiEbXfUk\/s640\/pki1.gif","link":"https:\/\/software-engineer-tips-and-tricks.blogspot.com\/2012\/09\/what-is-pki.html","title":"What is PKI","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Ph1gyTl8JUF_WrqVzvsRuQHaGv&pid=15.1","size":"500 x 455 \u00b7 gif","desc":"pki kerja \uad6c\uc131\ub3c4 sertifikat certificado \uc0ac\uc6a9 zertifikate atitude reflexiva","filetype":"gif","width":500,"height":455,"domain":"software-engineer-tips-and-tricks.blogspot.com","created_at":null,"updated_at":null,"id":1166,"keyword_id":79,"url":"https:\/\/cheapsslsecurity.com\/blog\/wp-content\/uploads\/2016\/07\/pki-components.jpg","link":"http:\/\/cheapsslsecurity.com\/blog\/understanding-the-role-of-certificate-authorities-in-pki\/","title":"Understanding the Role of Certificate Authority in PKI","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.0sr_cJ99OWhq_Fd5S6KgQQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki infrastructure certification","filetype":"jpg","width":638,"height":479,"domain":"cheapsslsecurity.com","created_at":null,"updated_at":null,"id":1167,"keyword_id":79,"url":"https:\/\/www.thesslstore.com\/blog\/wp-content\/uploads\/2017\/08\/iStock-597931354.jpg","link":"https:\/\/www.thesslstore.com\/blog\/wide-world-pki\/","title":"Understanding Public Key Infrastructure: The Wide World of PKI","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.mT29JSIgQUwuO-Jd7o6JKAHaEK&pid=15.1","size":"1365 x 768 \u00b7 jpeg","desc":"pki wide key infrastructure hashed re trust","filetype":"jpg","width":1365,"height":768,"domain":"www.thesslstore.com","created_at":null,"updated_at":null, PKI Fundamentals","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.xnQ0uSJS0VBwRW3-XLh1nQHaEH&pid=15.1","size":"1280 x 711 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":1280,"height":711,"domain":"www.encryptionconsulting.com","created_at":null,"updated_at":null,"id":1169,"keyword_id":79,"url":"http:\/\/pki-tutorial.readthedocs.io\/en\/latest\/_images\/AdvancedPKILayout.png","link":"http:\/\/pki-tutorial.readthedocs.io\/en\/latest\/advanced\/","title":"Advanced PKI \u2014 OpenSSL PKI Tutorial","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.3rR6uFxdGU-PcLDbZ5wRtgAAAA&pid=15.1","size":"467 x 422 \u00b7 png","desc":"pki advanced tutorial root openssl pronged runs serve needs security readthedocs three its latest io","filetype":"png","width":467,"height":422,"domain":"pki-tutorial.readthedocs.io","created_at":null,"updated_at":null,"id":1170,"keyword_id":79,"url":"https:\/\/www.codegic.com\/wp-content\/uploads\/2021\/05\/PKI-Hierarchy.jpg","link":"https:\/\/www.codegic.com\/learn-public-key-infrastructure-pki-basics-part-1\/","title":"Learn Public Key Infrastructure (PKI) Basics - Part 1 - Codegic","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Z6x0M_b19rKZonQPZkzoCAHaGg&pid=15.1","size":"482 x 424 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":482,"height":424,"domain":"www.codegic.com","created_at":null,"updated_at":null,"id":1171,"keyword_id":79,"url":"http:\/\/www.jnsa.org\/mpki\/intro_pkimodels.png","link":"http:\/\/www.jnsa.org\/mpki\/","title":"Welcome! - Challenge PKI Project","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.mh0PKUmxOknvsHwx5DaZkAHaEe&pid=15.1","size":"459 x 277 \u00b7 png","desc":"pki scheme federal very","filetype":"png","width":459,"height":277,"domain":"www.jnsa.org","created_at":null,"updated_at":null, Mastering OpenVPN","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.7FaGaDK23CmXcf3ppEOF2gHaHq&pid=15.1","size":"600 x 621 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":600,"height":621,"domain":"subscription.packtpub.com","created_at":null,"updated_at":null,"id":1173,"keyword_id":79,"url":"https:\/\/www.h3c.com\/en\/res\/200706\/01\/20070601_108248_image001_205817_1285_0.gif","link":"https:\/\/www.h3c.com\/en\/Support\/Resource_Center\/HK\/Switches\/H3C_S5500\/H3C_S5500_Series_Switches\/Technical_Documents\/Configure\/Configuration_Guides\/H3C_S5500-SI_OM-Release_1205(V1.03)\/200706\/205817_294551_0.htm","title":"Support - 31-PKI Operation- H3C","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.-tfxx5J752FQOpqvmq9aSwHaF6&pid=15.1","size":"391 x 312 \u00b7 gif","desc":"pki h3c architecture figure configuration","filetype":"gif","width":391,"height":312,"domain":"www.h3c.com","created_at":null,"updated_at":null,"id":1174,"keyword_id":79,"url":"https:\/\/image.slidesharecdn.com\/overallcryptographyandpkiupdate-121009014046-phpapp02\/95\/overall-cryptography-and-pki-introduction-19-728.jpg?cb=1349746915","link":"https:\/\/www.slideshare.net\/mita29\/overall-cryptography-and-pki-introduction","title":"Overall cryptography and pki introduction","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.JSFJ0Qpa_x6_EyLiWKFs2gHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"pki cryptography encryption","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1175,"keyword_id":79,"url":"http:\/\/3.bp.blogspot.com\/-ZSop4-5-vzM\/UagiaOddIBI\/AAAAAAAADmk\/gKVIf5sR8kM\/s1600\/dn+aidit.jpg","link":"http:\/\/beranimimpi.blogspot.com\/2013\/06\/dn-aidit-pemimpin-partai-komunis.html","title":"D.N. AIDIT (Pemimpin Partai Komunis Indonesia) - Success = Dream x Work","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.b0YbvQfET-EBkZJn3At4_AAAAA&pid=15.1","size":"392 x 600 \u00b7 jpeg","desc":"aidit pki komunis pahlawan revolusi jenazah partai misteri rossrightangle pemimpin nusantara terkuak candu agama aidat paham indocropcircles perintah supersemar maret","filetype":"jpg","width":392,"height":600,"domain":"beranimimpi.blogspot.com","created_at":null,"updated_at":null,"id":1176,"keyword_id":79,"url":"http:\/\/www.iot-now.com\/wp-content\/uploads\/2016\/04\/Strong-device-identity-image-GlobalSign.jpg","link":"http:\/\/www.iot-now.com\/2016\/04\/27\/46520-addressing-key-iot-security-concerns-for-manufacturers\/","title":"Addressing key IoT security concerns for manufacturers - IoT Now - How","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.dhaSjRuhCCd9tiF-xLYvrAHaE8&pid=15.1","size":"1701 x 1134 \u00b7 jpeg","desc":"iot security key concerns addressing manufacturers device identity strong","filetype":"jpg","width":1701,"height":1134,"domain":"www.iot-now.com","created_at":null,"updated_at":null, ESCRYPT","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.kBkEIUD9Ci-EGDDTt1FeAwHaEr&pid=15.1","size":"842 x 532 \u00b7 jpeg","desc":"tisax escrypt kaizen \u8a8d\u8a3c \u5408\u683c","filetype":"jpg","width":842,"height":532,"domain":"www.escrypt.com","created_at":null,"updated_at":null,"id":1178,"keyword_id":79,"url":"https:\/\/www.escrypt.com\/sites\/default\/files\/2020-02\/AUTOSAR_security_0.jpg","link":"https:\/\/www.escrypt.com\/en\/news-events\/autosar_security","title":"AUTOSAR security: Achieving integrated cybersecurity with the Adaptive","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.e0HzhQZQj4U10-Or00POLgHaEr&pid=15.1","size":"843 x 532 \u00b7 jpeg","desc":"autosar security adaptive achieving cybersecurity integrated platform","filetype":"jpg","width":843,"height":532,"domain":"www.escrypt.com","created_at":null,"updated_at":null,"id":1179,"keyword_id":79,"url":"https:\/\/present5.com\/presentation\/534fb19deda8d661a65743880572bcb7\/image-139.jpg","link":"https:\/\/present5.com\/the-internet-overview-an-introduction-to\/","title":"The Internet Overview An introduction to","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.NMnfYG78ZnDwKImu6Ww4eAHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"","filetype":"jpg","width":720,"height":540,"domain":"present5.com","created_at":null,"updated_at":null,"id":1180,"keyword_id":79,"url":"https:\/\/present5.com\/presentation\/534fb19deda8d661a65743880572bcb7\/image-42.jpg","link":"https:\/\/present5.com\/the-internet-overview-an-introduction-to\/","title":"The Internet Overview An introduction to","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.xVvQGlgNXQTKlgZJdrqptAHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"introduction overview internet advertisements","filetype":"jpg","width":720,"height":540,"domain":"present5.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about pki system Understanding the role of certificate authority in pki. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment