If you are searching about Public Key Infrastructure (PKI) services in Delhi, NCR you've visit to the right web. We have 17 Images about Public Key Infrastructure (PKI) services in Delhi, NCR like How PKI Works ? - Technical Blog | REBELADMIN, Public Key Infrastructure (PKI) services in Delhi, NCR and also Cybersecurity Salary in Washington, D.C. Metro Infographic. Here it is:
Public Key Infrastructure (PKI) Services In Delhi, NCR
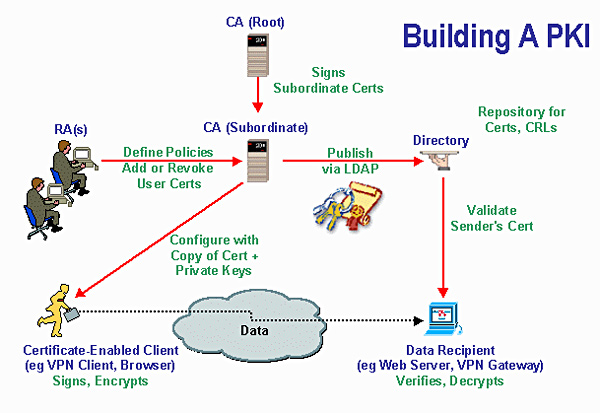 fspl.co.in
fspl.co.in pki
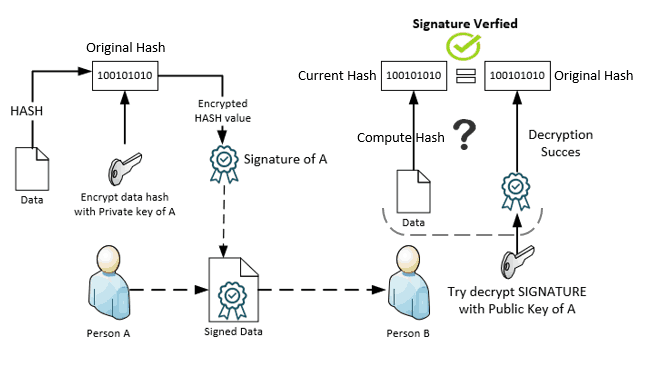
Digital Signature Scheme For Email Messages
signature digital process email ghacks diagram traffic pki scheme smime abu farah encrypt sign mail
Cybersecurity Salary In Washington, D.C. Metro Infographic
 news.clearancejobs.com
news.clearancejobs.com cybersecurity infographic salary metro washington dc jobs clearancejobs cleared security clearance salaries visual compensation penetration tester embed engineer
Large IT Infrastructure (e.g. PKI) – Cyberplc
 www.cyberplc.com
www.cyberplc.com pki entity inspect
SSL Certificate - How And What Are They Used For
authentication certificate mutual process certificates does between security steps using tls server client based works handshake step secure private connection
How PKI Works
 godinus123.blogspot.com
godinus123.blogspot.com pki works followed sake understanding added
TechComm - A Technical Communicator's Blog: Public Key Infrastructure
 tech-writing-space.blogspot.com
tech-writing-space.blogspot.com pki key infrastructure technical purpose data
Opto-Acoustic Laser Microphone | PKI Electronic Intelligence GmbH Germany
laser microphone opto electronic acoustic pki surveillance equipment 2510 audio
How PKI Works ? - RebelAdmin.com
pki works rebeladmin
The Internet Overview An Introduction To
 present5.com
present5.com Integrating External Document Repositories With SharePoint Server 2007
sharepoint document external repository repositories server integrating 2007
PKI Framework For Supporting The Security Of Mobile Communication From
pki security framework certificate authentication system certification mobile infrastructure key authority certificates supporting communication core its certs infra trusted organizations
URLs
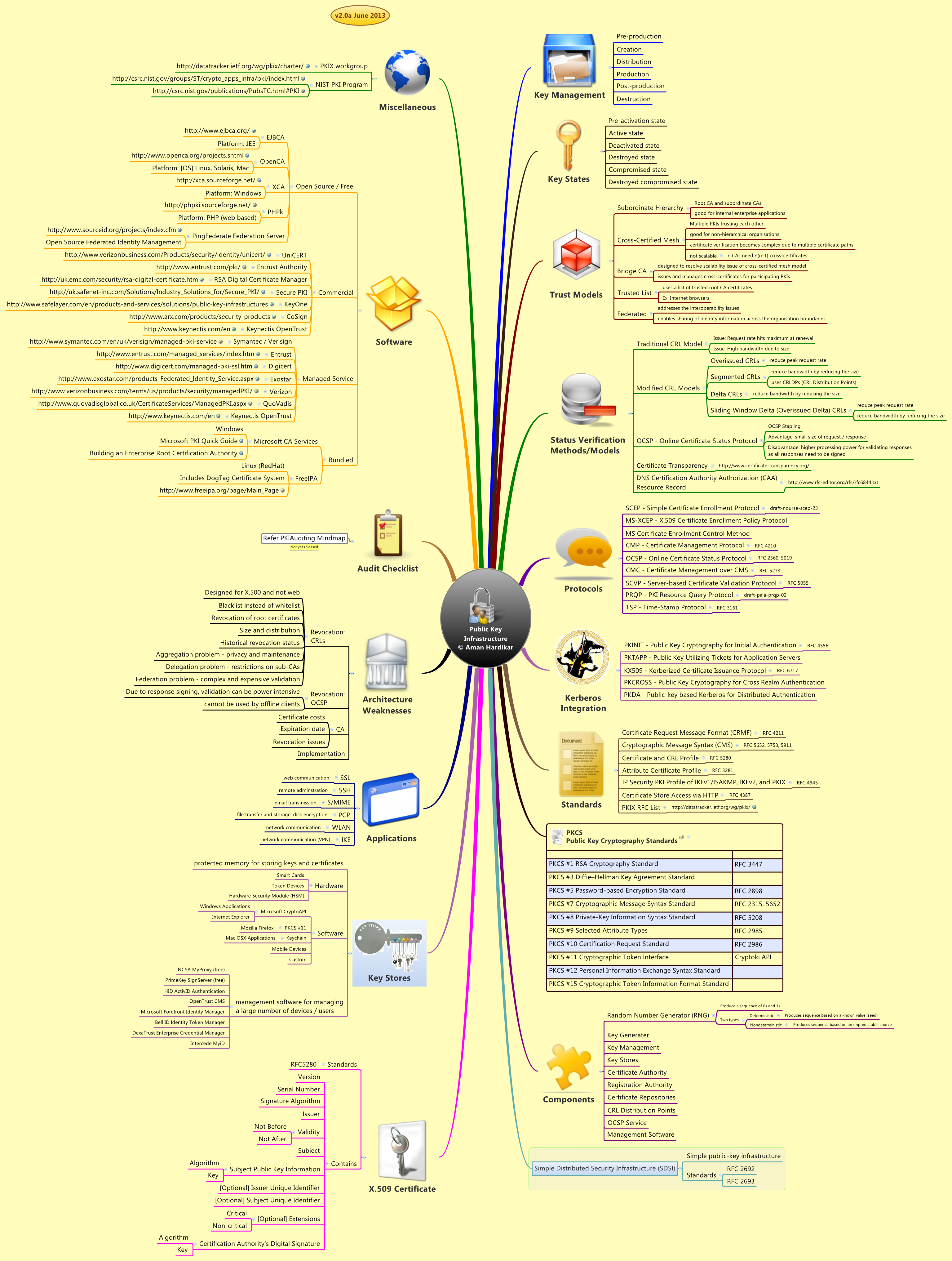 www.amanhardikar.com
www.amanhardikar.com pki mind mindmaps maps ton posters awesome key ending security never
Introduction To PKI Technology
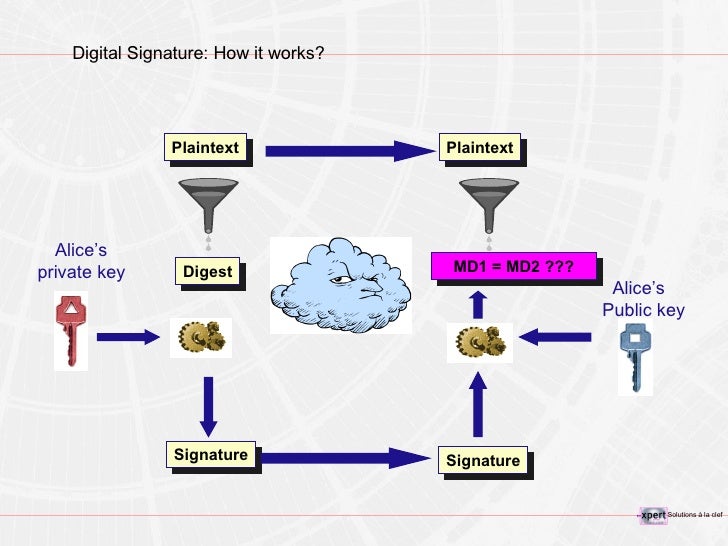 www.slideshare.net
www.slideshare.net pki technology
Learn The Basic Concepts Of PKI - Intune PKI Made Easy With Joy Part-1
 www.anoopcnair.com
www.anoopcnair.com pki intune
How PKI Works ? - Technical Blog | REBELADMIN
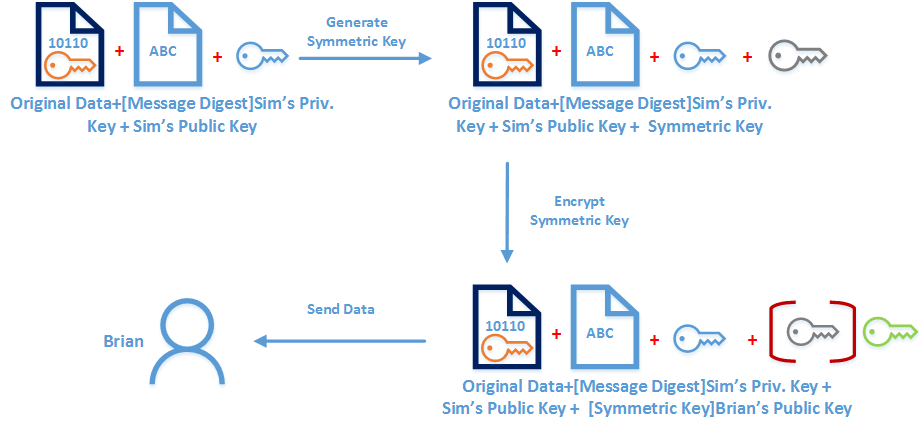 www.rebeladmin.com
www.rebeladmin.com pki works process rebeladmin
DocuSign | Digital Harbour
 digitalharbour.com.sg
digitalharbour.com.sg docusign audit trail
Cybersecurity salary in washington, d.c. metro infographic. How pki works ?. Pki works rebeladmin
if you are looking "id":102,"keyword_id":2,"name":"PKI Process","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1611,"keyword_id":102,"url":"https:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/pki6.png","link":"https:\/\/www.rebeladmin.com\/2018\/05\/how-pki-works\/","title":"How PKI Works ? - Technical Blog ,"id":1612,"keyword_id":102,"url":"https:\/\/fspl.co.in\/wp-content\/uploads\/2018\/11\/pki-2.jpg","link":"http:\/\/fspl.co.in\/digitization\/pki\/","title":"Public Key Infrastructure (PKI) services in Delhi, NCR","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.vk1RQLVk1lF2KzEiWZqopgHaFG&pid=15.1","size":"600 x 413 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":600,"height":413,"domain":"fspl.co.in","created_at":null,"updated_at":null,"id":1613,"keyword_id":102,"url":"http:\/\/tweenpath.net\/wp-content\/uploads\/PKI.gif","link":"http:\/\/tweenpath.net\/pki-framework-for-supporting-the-security-of-mobile-communication-from-its-core\/","title":"PKI Framework for Supporting the Security of Mobile Communication from","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.Ph1gyTl8JUF_WrqVzvsRuQHaGv&pid=15.1","size":"500 x 455 \u00b7 gif","desc":"pki security framework certificate authentication system certification mobile infrastructure key authority certificates supporting communication core its certs infra trusted organizations","filetype":"gif","width":500,"height":455,"domain":"tweenpath.net","created_at":null,"updated_at":null,"id":1614,"keyword_id":102,"url":"https:\/\/4.bp.blogspot.com\/-pofx1OtKB0Q\/W7gk50XTQhI\/AAAAAAAGS1Q\/x2KfFHW4Bm06yZxuHoNM6DhBSbTZZcY8gCLcBGAs\/s1600\/PKI.png","link":"https:\/\/godinus123.blogspot.com\/2018\/10\/active-directory-how-pki-works-may-13.html","title":"How PKI Works","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.jqPNnuOHs7rVWLfd31UG5gHaDt&pid=15.1","size":"759 x 381 \u00b7 png","desc":"pki works followed sake understanding added","filetype":"png","width":759,"height":381,"domain":"godinus123.blogspot.com","created_at":null,"updated_at":null,"id":1615,"keyword_id":102,"url":"http:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/pki2.png","link":"https:\/\/www.rebeladmin.com\/2018\/05\/how-pki-works\/","title":"How PKI Works ? - RebelAdmin.com","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.GAoWsu5YVl2rrepP5K5sWQHaE5&pid=15.1","size":"534 x 353 \u00b7 png","desc":"pki works rebeladmin","filetype":"png","width":534,"height":353,"domain":"www.rebeladmin.com","created_at":null,"updated_at":null,"id":1616,"keyword_id":102,"url":"https:\/\/www.anoopcnair.com\/wp-content\/uploads\/2020\/04\/PKI-4.png","link":"https:\/\/www.anoopcnair.com\/pki-basics-intune-pki-made-easy-with-joy-1\/","title":"Learn The Basic Concepts Of PKI - Intune PKI Made Easy With Joy Part-1","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.yyEtbSTFMfTaEavKeKVxFwHaEP&pid=15.1","size":"647 x 370 \u00b7 png","desc":"pki intune","filetype":"png","width":647,"height":370,"domain":"www.anoopcnair.com","created_at":null,"updated_at":null,"id":1617,"keyword_id":102,"url":"http:\/\/3.bp.blogspot.com\/_rJ3o-NvDomo\/TE2neY-W6BI\/AAAAAAAAANs\/PM61HFngbEA\/s1600\/pki-diagram1.jpg","link":"http:\/\/tech-writing-space.blogspot.com\/2010\/07\/public-key-infrastructure.html","title":"TechComm - A Technical Communicator's Blog: Public Key Infrastructure","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.7wNrR__wyP56I8eGgID2MgAAAA&pid=15.1","size":"429 x 295 \u00b7 jpeg","desc":"pki key infrastructure technical purpose data","filetype":"jpg","width":429,"height":295,"domain":"tech-writing-space.blogspot.com","created_at":null,"updated_at":null,"id":1618,"keyword_id":102,"url":"https:\/\/www.amanhardikar.com\/mindmaps\/PKI.png","link":"https:\/\/www.amanhardikar.com\/mindmaps\/PKI.html","title":"URLs","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.wqRMFtcU-hvQm3OTqT0MygHaJz&pid=15.1","size":"3071 x 4066 \u00b7 png","desc":"pki mind mindmaps maps ton posters awesome key ending security never","filetype":"png","width":3071,"height":4066,"domain":"www.amanhardikar.com","created_at":null,"updated_at":null,"id":1619,"keyword_id":102,"url":"http:\/\/www.herongyang.com\/PKI\/SMIME-Digital-Signature-Process.jpg","link":"http:\/\/www.herongyang.com\/PKI\/SMIME-Digital-Signature-Scheme-for-Email-Messages.html","title":"Digital Signature Scheme for Email Messages","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.BBAki2L2AUjP8-B-vm4ZOwHaEc&pid=15.1","size":"500 x 300 \u00b7 jpeg","desc":"signature digital process email ghacks diagram traffic pki scheme smime abu farah encrypt sign mail","filetype":"jpg","width":500,"height":300,"domain":"www.herongyang.com","created_at":null,"updated_at":null,"id":1620,"keyword_id":102,"url":"https:\/\/www.cyberplc.com\/wp-content\/uploads\/2013\/08\/Simplified-PKI-v03.jpg","link":"https:\/\/www.cyberplc.com\/what-we-do\/large-it-infrastructure-e-g-pki\/","title":"Large IT Infrastructure (e.g. PKI) \u2013 Cyberplc","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.sIpVhx0FZ0QOODNA_xTvOQHaH4&pid=15.1","size":"663 x 706 \u00b7 jpeg","desc":"pki entity inspect","filetype":"jpg","width":663,"height":706,"domain":"www.cyberplc.com","created_at":null,"updated_at":null,"id":1621,"keyword_id":102,"url":"https:\/\/image.slidesharecdn.com\/introductiontopkitechnology-090502145056-phpapp02\/95\/introduction-to-pki-technology-88-728.jpg?cb=1241276083","link":"https:\/\/www.slideshare.net\/smaret\/introduction-to-pki-technology","title":"Introduction To PKI Technology","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.3AnI-JCjKKgEeO_wGDtW4AEgDY&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"pki technology","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1622,"keyword_id":102,"url":"http:\/\/i.stack.imgur.com\/1lWyn.png","link":"https:\/\/www.verticalrail.com\/kb\/ssl-certificates\/","title":"SSL Certificate - How and What are They Used for","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.9n4iNgO2uX6iS29ufVxV1QHaFt&pid=15.1","size":"813 x 627 \u00b7 png","desc":"authentication certificate mutual process certificates does between security steps using tls server client based works handshake step secure private connection","filetype":"png","width":813,"height":627,"domain":"www.verticalrail.com","created_at":null,"updated_at":null,"id":1623,"keyword_id":102,"url":"https:\/\/4d0q7u11k31p1qnkosal8q2e-wpengine.netdna-ssl.com\/wp-content\/uploads\/2013\/10\/ClearanceJobs_Cybersecurity_Infographic.png","link":"https:\/\/news.clearancejobs.com\/cybersecurity-salary-in-dc-metro-infographic\/","title":"Cybersecurity Salary in Washington, D.C. Metro Infographic","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.u7vR3IiiD5jUnjQuSjAQYgHaEy&pid=15.1","size":"1500 x 971 \u00b7 png","desc":"cybersecurity infographic salary metro washington dc jobs clearancejobs cleared security clearance salaries visual compensation penetration tester embed engineer","filetype":"png","width":1500,"height":971,"domain":"news.clearancejobs.com","created_at":null,"updated_at":null,"id":1624,"keyword_id":102,"url":"http:\/\/www.agileit.com\/wp-content\/uploads\/Dd440954.7a81a773-56cb-44a8-be6b-c9016992fda1en-usoffice.12.jpg","link":"http:\/\/www.agileit.com\/news\/integrating-external-document-repositories-with-sharepoint-server-2007\/","title":"Integrating External Document Repositories with SharePoint Server 2007","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.51xJ0yWA0zOjCESQMvGiPQHaEF&pid=15.1","size":"511 x 282 \u00b7 jpeg","desc":"sharepoint document external repository repositories server integrating 2007","filetype":"jpg","width":511,"height":282,"domain":"www.agileit.com","created_at":null,"updated_at":null,"id":1625,"keyword_id":102,"url":"http:\/\/www.pki-electronic.com\/wp-content\/uploads\/2012\/04\/2510.jpg","link":"http:\/\/www.pki-electronic.com\/products\/audio-surveillance-equipment\/opto-acoustic-laser-microphone\/","title":"Opto-Acoustic Laser Microphone , Digital Harbour","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.soQGViVKNy13uJoDOvWm_wHaET&pid=15.1","size":"576 x 335 \u00b7 png","desc":"docusign audit trail","filetype":"png","width":576,"height":335,"domain":"digitalharbour.com.sg","created_at":null,"updated_at":null,"id":1627,"keyword_id":102,"url":"https:\/\/present5.com\/presentation\/534fb19deda8d661a65743880572bcb7\/image-129.jpg","link":"https:\/\/present5.com\/the-internet-overview-an-introduction-to\/","title":"The Internet Overview An introduction to","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.lBUYbkfXp31-ELvDGovnGgHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"","filetype":"jpg","width":720,"height":540,"domain":"present5.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Process Large it infrastructure (e.g. pki) – cyberplc. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment