If you are searching about Chapter 7: The Role of Cryptography in Information Security - InfoSec you've visit to the right place. We have 16 Pictures about Chapter 7: The Role of Cryptography in Information Security - InfoSec like What Is PKI (Public Key Infrastructure), fred's integration blog: July 2009 and also An introduction to SwiftNET. Here it is:
Chapter 7: The Role Of Cryptography In Information Security - InfoSec
cryptography key role private keys encryption
What Is PKI (Public Key Infrastructure)
pki infrastructure key flow process introduction
Public Key Infrastructure And Authentication | Jisc Community
authentication infrastructure key community jisc pki demonstration structures graphic figure
Private Vs Public PKI: Building An Effective Plan - SSL.com
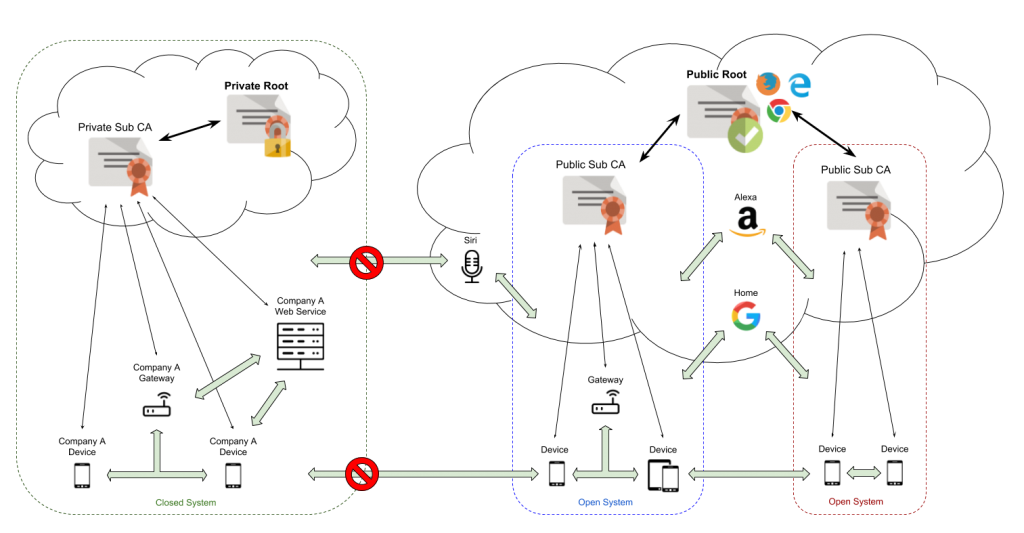 www.ssl.com
www.ssl.com pki
PKI Architecture
 techhub.hpe.com
techhub.hpe.com pki architecture entity
Patent US20030056099 - Public Key Infrastructure (PKI) Based System
 www.google.de
www.google.de bilder patentsuche
Public Key Infrastructure (PKI) - JEFF HOWELL
pki key infrastructure definition
How Does PKI Infrastructure Work? - IMC Grupo
 www.imcgrupo.com
www.imcgrupo.com pki securing
Creating A Safe And Secure Network Society Using Digital Certificates
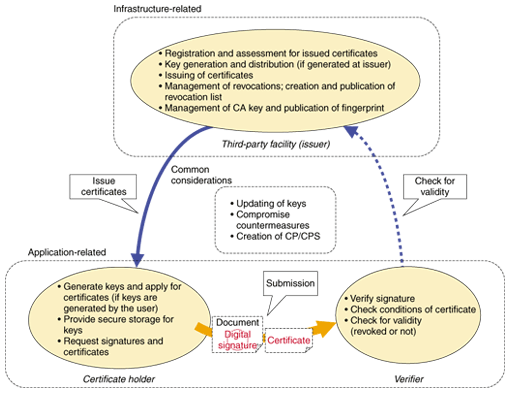 www.ntt-review.jp
www.ntt-review.jp pki ntt considerations fig roles architectural elements
Fred's Integration Blog: July 2009
 another-soa-blog.blogspot.com
another-soa-blog.blogspot.com pki certificate integration fred usage figure
An Introduction To SwiftNET
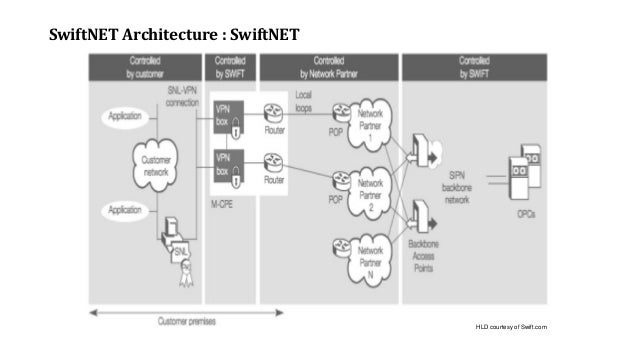 www.slideshare.net
www.slideshare.net swiftnet
Public Key Infrastructure – IQUANTICS
infrastructure key security
Public Key Infrastructure PKI – Tec-Bite IT-Security Blog
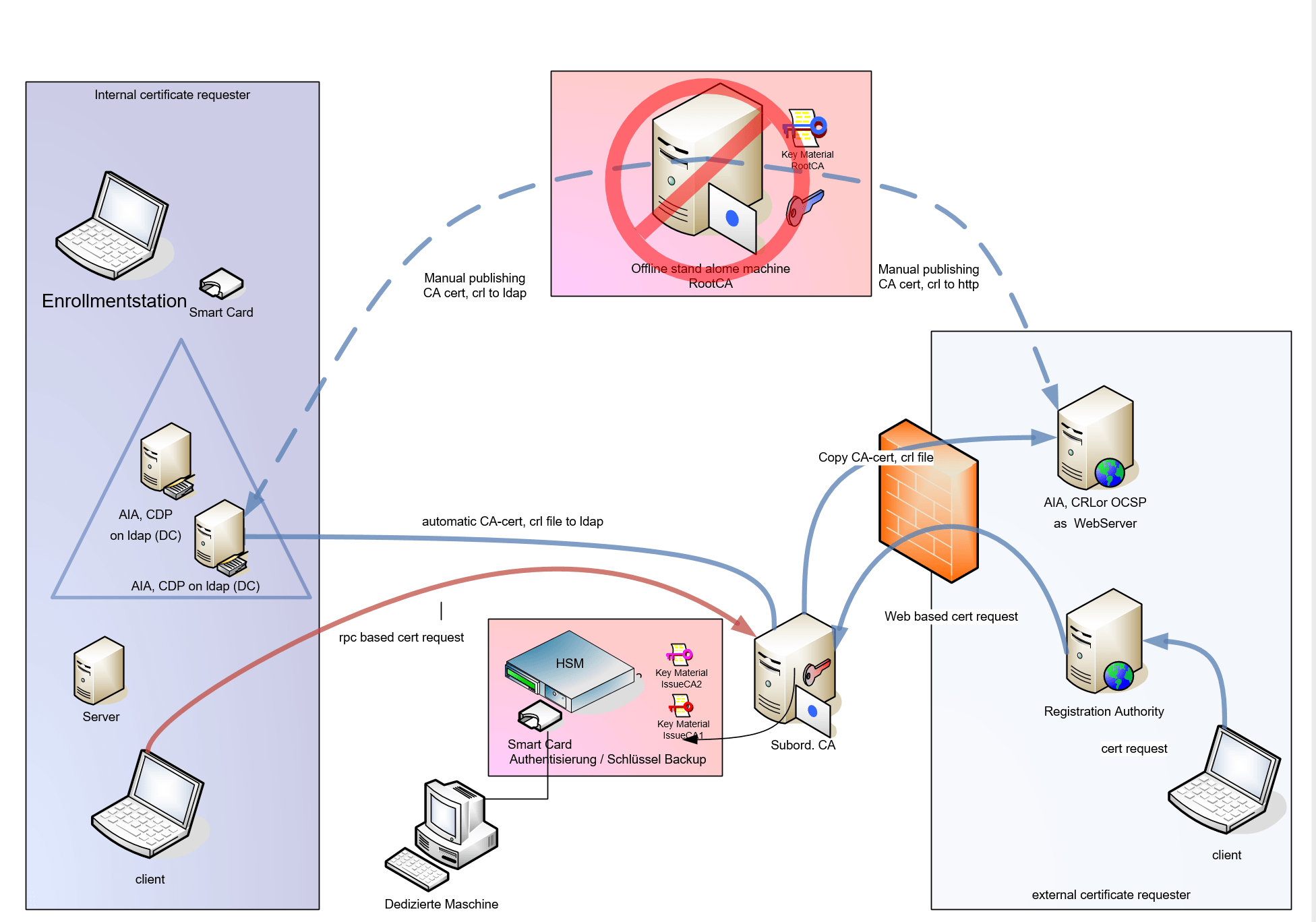 www.avantec.ch
www.avantec.ch pki hsm grundstruktur cdps dargestellt generellen aias enrolment
Understanding And Implementing PKI With OpenSSL | ThinkBox
 blog.thinkbox.dev
blog.thinkbox.dev pki openssl diagram thinkbox implementing understanding
Patent US20030046362 - System, Method And Computer Product For PKI
 www.google.ca
www.google.ca patents claims
SecurityWorldMag.com - A Gateway To Global Security Industry
icao pki temporal
Understanding and implementing pki with openssl. Public key infrastructure and authentication. Bilder patentsuche
if you are looking "id":77,"keyword_id":2,"name":"pki infrastructure diagram","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1199,"keyword_id":77,"url":"http:\/\/www.herongyang.com\/PKI\/PKI_Introduction.jpg","link":"http:\/\/www.herongyang.com\/PKI\/Introduction-What-Is-PKI-Public-Key-Infrastructure.html","title":"What Is PKI (Public Key Infrastructure)","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.dVAiEXBhg_-GgdgyS6VW4AHaFL&pid=15.1","size":"427 x 299 \u00b7 jpeg","desc":"pki infrastructure key flow process introduction","filetype":"jpg","width":427,"height":299,"domain":"www.herongyang.com","created_at":null,"updated_at":null,"id":1200,"keyword_id":77,"url":"http:\/\/1.bp.blogspot.com\/_tebyDeNhwDs\/SlNyTZvmgEI\/AAAAAAAAABo\/nROxF19_tKk\/s400\/image005.png","link":"http:\/\/another-soa-blog.blogspot.com\/2009_07_01_archive.html","title":"fred's integration blog: July 2009","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.faPIvchYveX4yPuGjaQD2AAAAA&pid=15.1","size":"400 x 344 \u00b7 png","desc":"pki certificate integration fred usage figure","filetype":"png","width":400,"height":344,"domain":"another-soa-blog.blogspot.com","created_at":null,"updated_at":null,"id":1201,"keyword_id":77,"url":"http:\/\/www.iquantics.com\/wp-content\/uploads\/2015\/12\/infraestructuraclavepublicaEng.png","link":"https:\/\/www.iquantics.com\/index.php\/en\/public-key-infrastructure\/","title":"Public Key Infrastructure \u2013 IQUANTICS","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.KWUq8LPefWPJjyCT_lKNCAHaEf&pid=15.1","size":"985 x 598 \u00b7 png","desc":"infrastructure key security","filetype":"png","width":985,"height":598,"domain":"www.iquantics.com","created_at":null,"updated_at":null,"id":1202,"keyword_id":77,"url":"https:\/\/d1smxttentwwqu.cloudfront.net\/wp-content\/uploads\/2018\/09\/public_vs_private_diagram-1024x533.png","link":"https:\/\/www.ssl.com\/article\/private-vs-public-pki-building-an-effective-plan\/","title":"Private vs Public PKI: Building an Effective Plan - SSL.com","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.GWsSxl8PzIKvMazdpr8OFQHaD2&pid=15.1","size":"1024 x 533 \u00b7 png","desc":"pki","filetype":"png","width":1024,"height":533,"domain":"www.ssl.com","created_at":null,"updated_at":null,"id":1203,"keyword_id":77,"url":"https:\/\/www.tec-bite.ch\/wp-content\/uploads\/2020\/10\/grundstruktur-pki.png","link":"https:\/\/www.avantec.ch\/public-key-infrastructure-wies-funktioniert-und-leitfragen-fuer-die-implementierung\/","title":"Public Key Infrastructure PKI \u2013 Tec-Bite IT-Security Blog","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.4wEA5c2hSkwOTOzySh4lBAHaFM&pid=15.1","size":"1952 x 1368 \u00b7 png","desc":"pki hsm grundstruktur cdps dargestellt generellen aias enrolment","filetype":"png","width":1952,"height":1368,"domain":"www.avantec.ch","created_at":null,"updated_at":null, ThinkBox","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.OTu8WnHhxkWiMiQFgP4kdAAAAA&pid=15.1","size":"461 x 261 \u00b7 png","desc":"pki openssl diagram thinkbox implementing understanding","filetype":"png","width":461,"height":261,"domain":"blog.thinkbox.dev","created_at":null,"updated_at":null,"id":1205,"keyword_id":77,"url":"https:\/\/www.imcgrupo.com\/wp-content\/uploads\/2021\/02\/Picture1.png","link":"https:\/\/www.imcgrupo.com\/how-does-pki-infrastructure-work\/","title":"How Does PKI Infrastructure Work? - IMC Grupo","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.S3XZLEjDG571V0h-nqwX7QHaDJ&pid=15.1","size":"975 x 414 \u00b7 png","desc":"pki securing","filetype":"png","width":975,"height":414,"domain":"www.imcgrupo.com","created_at":null,"updated_at":null,"id":1206,"keyword_id":77,"url":"http:\/\/www.jeffreyahowell.com\/uploads\/9\/7\/7\/3\/97736672\/published\/pki.png?1528648239","link":"http:\/\/www.jeffreyahowell.com\/public-key-infrastructure-pki.html","title":"Public Key Infrastructure (PKI) - JEFF HOWELL","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.6k9Sm4yIrTVqjFI7YwG39wAAAA&pid=15.1","size":"231 x 158 \u00b7 png","desc":"pki key infrastructure definition","filetype":"png","width":231,"height":158,"domain":"www.jeffreyahowell.com","created_at":null,"updated_at":null,"id":1207,"keyword_id":77,"url":"https:\/\/techhub.hpe.com\/eginfolib\/networking\/docs\/switches\/5130ei\/5200-3946_security_cg\/content\/images\/image96.png","link":"https:\/\/techhub.hpe.com\/eginfolib\/networking\/docs\/switches\/5130ei\/5200-3946_security_cg\/content\/485048341.htm","title":"PKI architecture","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.vMp2nYOLpgdKOaOZj7z5vQAAAA&pid=15.1","size":"336 x 213 \u00b7 png","desc":"pki architecture entity","filetype":"png","width":336,"height":213,"domain":"techhub.hpe.com","created_at":null,"updated_at":null,"id":1208,"keyword_id":77,"url":"http:\/\/resources.infosecinstitute.com\/wp-content\/uploads\/061112_1445_Chapter7The11.jpg","link":"http:\/\/resources.infosecinstitute.com\/role-of-cryptography\/","title":"Chapter 7: The Role of Cryptography in Information Security - InfoSec","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.cUo3tE47XbCTqnQRwQlKewHaFE&pid=15.1","size":"516 x 353 \u00b7 jpeg","desc":"cryptography key role private keys encryption","filetype":"jpg","width":516,"height":353,"domain":"resources.infosecinstitute.com","created_at":null,"updated_at":null,"id":1209,"keyword_id":77,"url":"http:\/\/community.ja.net\/system\/files\/images\/tg-vpn-02.jpg","link":"https:\/\/community.jisc.ac.uk\/library\/advisory-services\/public-key-infrastructure-and-authentication","title":"Public Key Infrastructure and authentication ,"id":1210,"keyword_id":77,"url":"http:\/\/www.securityworldmag.com\/data_file\/board\/3(2).jpg","link":"http:\/\/www.securityworldmag.com\/wsr\/wsr_view.asp?idx=635&part_code=02&page=6","title":"SecurityWorldMag.com - A Gateway to Global Security Industry","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.S3VAdRnRk34-pOOjxPE2NgHaEB&pid=15.1","size":"889 x 483 \u00b7 jpeg","desc":"icao pki temporal","filetype":"jpg","width":889,"height":483,"domain":"www.securityworldmag.com","created_at":null,"updated_at":null,"id":1211,"keyword_id":77,"url":"https:\/\/www.ntt-review.jp\/archive_html\/200803\/images\/le1_fig07.gif","link":"https:\/\/www.ntt-review.jp\/archive\/ntttechnical.php?contents=ntr200803le1.html","title":"Creating a Safe and Secure Network Society Using Digital Certificates","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.bkLoMpdHc6Xb1YiNcnGIRAHaFt&pid=15.1","size":"510 x 393 \u00b7 gif","desc":"pki ntt considerations fig roles architectural elements","filetype":"gif","width":510,"height":393,"domain":"www.ntt-review.jp","created_at":null,"updated_at":null,"id":1212,"keyword_id":77,"url":"https:\/\/patentimages.storage.googleapis.com\/US20030046362A1\/US20030046362A1-20030306-D00007.png","link":"https:\/\/www.google.ca\/patents\/US20030046362","title":"Patent US20030046362 - System, method and computer product for PKI","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.3TnyH6sbHFrbvndLmAbK-AHaJR&pid=15.1","size":"2053 x 2570 \u00b7 png","desc":"patents claims","filetype":"png","width":2053,"height":2570,"domain":"www.google.ca","created_at":null,"updated_at":null,"id":1213,"keyword_id":77,"url":"https:\/\/patentimages.storage.googleapis.com\/US20030056099A1\/US20030056099A1-20030320-D00000.png","link":"https:\/\/www.google.de\/patents\/US20030056099","title":"Patent US20030056099 - Public key infrastructure (PKI) based system","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.8PemLub1sPGaXjK-ymWbIQEsDJ&pid=15.1","size":"2700 x 1809 \u00b7 png","desc":"bilder patentsuche","filetype":"png","width":2700,"height":1809,"domain":"www.google.de","created_at":null,"updated_at":null,"id":1214,"keyword_id":77,"url":"https:\/\/image.slidesharecdn.com\/swiftnet-public-plain-160519071128\/95\/an-introduction-to-swiftnet-18-638.jpg?cb=1463642127","link":"http:\/\/www.slideshare.net\/rishabhd\/an-introduction-to-swiftnet","title":"An introduction to SwiftNET","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.S85ElgxFPI9OwMo645AwOwHaEK&pid=15.1","size":"638 x 359 \u00b7 jpeg","desc":"swiftnet","filetype":"jpg","width":638,"height":359,"domain":"www.slideshare.net","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about pki infrastructure diagram Pki securing. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment