If you are looking for RO-PKI proposed architecture. | Download Scientific Diagram you've came to the right page. We have 18 Images about RO-PKI proposed architecture. | Download Scientific Diagram like Wireless PKI Architecture [9] | Download Scientific Diagram, (PDF) On the Performance Evaluation of Vehicular PKI Protocol for V2X and also Peter Kiewit Institute - Alley Poyner Macchietto Architecture. Here it is:
RO-PKI Proposed Architecture. | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net pki nco respect infrastructure outsourced
Cipher - Architecture
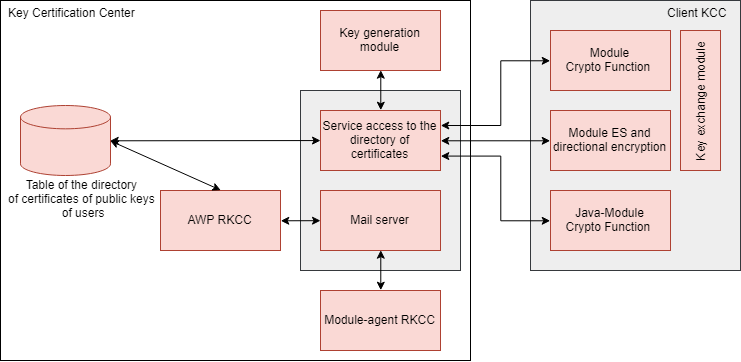 cipher.com.ua
cipher.com.ua pki cipher
OpenvSwitch Vs OpenFlow: What Are They, What's Their Relationship?
openvswitch openflow architecture vs relationship optic fiber
Peter Kiewit Institute - Alley Poyner Macchietto Architecture
 www.alleypoyner.com
www.alleypoyner.com peter institute kiewit apma omaha
Smart Metering Infrastructure Architecture And Analytics
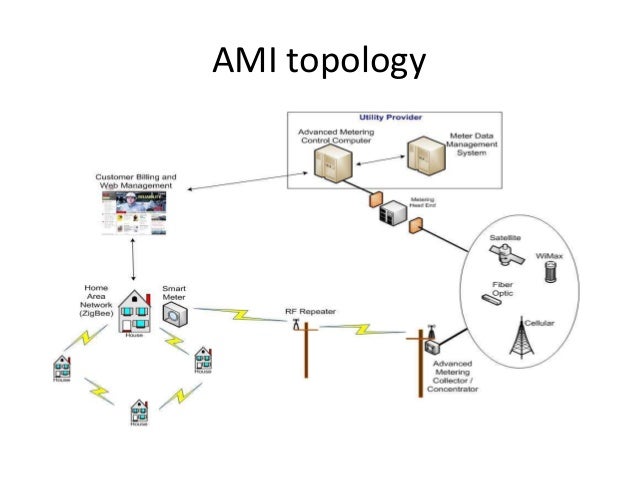 www.slideshare.net
www.slideshare.net metering analytics
Pka Architects - Precision Images
 www.precisionimages.com
www.precisionimages.com pka
(PDF) E-governance Public Key Infrastructure (PKI) Model
 www.researchgate.net
www.researchgate.net pki infrastructure key governance
Wireless PKI Architecture [9] | Download Scientific Diagram
![Wireless PKI Architecture [9] | Download Scientific Diagram](https://www.researchgate.net/profile/Chan-Yeun/publication/228651989/figure/download/fig1/AS:669406761848840@1536610417872/Wireless-PKI-Architecture-9.png) www.researchgate.net
www.researchgate.net pki
PKIについて整理しました - 家studyをつづって
 www.iestudy.work
www.iestudy.work Traditional PKI Architectures | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net pki architectures
Public Key Infrastructure Is Expected To Support Larger Numbers Of...
 securecommunications.airbus.com
securecommunications.airbus.com pki building trusted networks experts meet
(PDF) On The Performance Evaluation Of Vehicular PKI Protocol For V2X
 www.researchgate.net
www.researchgate.net pki v2x ise vehicular protocol certificates
StrongAuth PKI2FIDO Download | SourceForge.net
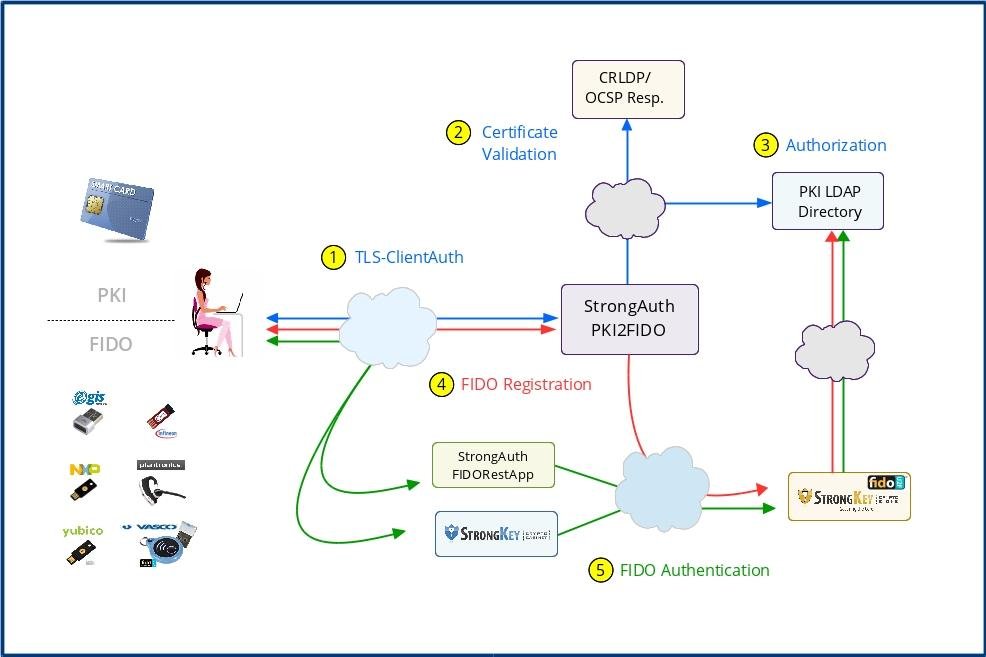 sourceforge.net
sourceforge.net screenshots architecture app
PKI Event
 cutting-edge-cybersec.com
cutting-edge-cybersec.com pki
Implementing Public Key Infrastructure
infrastructure key implementing pki overview
Microsoft PKI Services | Consulting Services | RNTrust
 www.rntrust.ae
www.rntrust.ae pki consulting microsoft services service ocsp
Education Center - Public Key Infrastructure | Venafi
 www.venafi.com
www.venafi.com pki
Security-Protocols-and-Standards | Magic's Blog
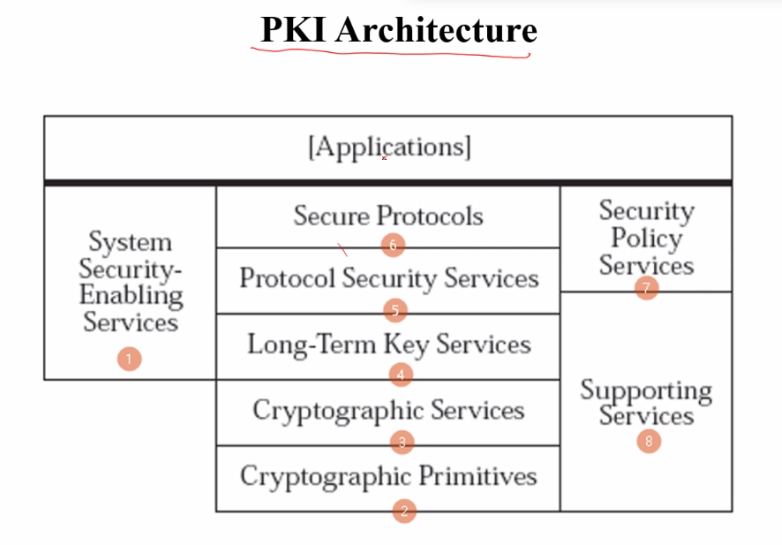 magic-king.net
magic-king.net pki protocols 系统 软件
Openvswitch openflow architecture vs relationship optic fiber. Peter kiewit institute. Pki consulting microsoft services service ocsp
if you are looking "id":106,"keyword_id":2,"name":"PKI Architecture","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1628,"keyword_id":106,"url":"https:\/\/www.researchgate.net\/profile\/Chan-Yeun\/publication\/228651989\/figure\/download\/fig1\/AS:669406761848840@1536610417872\/Wireless-PKI-Architecture-9.png","link":"https:\/\/www.researchgate.net\/figure\/Wireless-PKI-Architecture-9_fig1_228651989","title":"Wireless PKI Architecture [9] ,"id":1629,"keyword_id":106,"url":"https:\/\/www.researchgate.net\/profile\/Farah_Haidar3\/publication\/323135279\/figure\/fig1\/AS:734125875007492@1552040656882\/ISE-PKI-architecture_Q320.jpg","link":"https:\/\/www.researchgate.net\/publication\/323135279_On_the_Performance_Evaluation_of_Vehicular_PKI_Protocol_for_V2X_Communications_Security","title":"(PDF) On the Performance Evaluation of Vehicular PKI Protocol for V2X","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.N0D4LX8pTFQ4M_PDCUfLQgAAAA&pid=15.1","size":"320 x 320 \u00b7 jpeg","desc":"pki v2x ise vehicular protocol certificates","filetype":"jpg","width":320,"height":320,"domain":"www.researchgate.net","created_at":null,"updated_at":null,"id":1630,"keyword_id":106,"url":"https:\/\/a.fsdn.com\/con\/app\/proj\/pki2fido\/screenshots\/pki2fido.jpg","link":"https:\/\/sourceforge.net\/projects\/pki2fido\/","title":"StrongAuth PKI2FIDO download ,"id":1631,"keyword_id":106,"url":"https:\/\/cipher.com.ua\/media\/Products\/CipherPKI\/architecture-cipher-pki-Arch-cipher-PKI_en.png","link":"https:\/\/cipher.com.ua\/en\/products\/architecture-pki","title":"Cipher - Architecture","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.Wmyyse-qFy4c-ZuN5_oC-AHaDn&pid=15.1","size":"741 x 362 \u00b7 png","desc":"pki cipher","filetype":"png","width":741,"height":362,"domain":"cipher.com.ua","created_at":null,"updated_at":null, Download Scientific Diagram","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Mcb2p5GypJ_tD75F-jeOogHaCv&pid=15.1","size":"582 x 215 \u00b7 png","desc":"pki architectures","filetype":"png","width":582,"height":215,"domain":"www.researchgate.net","created_at":null,"updated_at":null, Venafi","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.V0KJlZVDI2ipTob-LXOu-gHaEK&pid=15.1","size":"1000 x 562 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":1000,"height":562,"domain":"www.venafi.com","created_at":null,"updated_at":null, Magic's Blog","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.fBUadmOs7o3i-zScb6KMtwHaFK&pid=15.1","size":"782 x 545 \u00b7 png","desc":"pki protocols \u7cfb\u7edf \u8f6f\u4ef6","filetype":"png","width":782,"height":545,"domain":"magic-king.net","created_at":null,"updated_at":null,"id":1635,"keyword_id":106,"url":"http:\/\/www.tech-faq.com\/wp-content\/uploads\/2010\/01\/implementing-public-key-infrastructure.jpeg","link":"http:\/\/www.tech-faq.com\/implementing-public-key-infrastructure.html","title":"Implementing Public Key Infrastructure","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.agl_k4SodK_zeFwv9UmiFQHaFF&pid=15.1","size":"271 x 186 \u00b7 jpeg","desc":"infrastructure key implementing pki overview","filetype":"jpg","width":271,"height":186,"domain":"www.tech-faq.com","created_at":null,"updated_at":null,"id":1636,"keyword_id":106,"url":"https:\/\/www.researchgate.net\/profile\/Jose_Montenegro7\/publication\/220905371\/figure\/fig3\/AS:667682319908873@1536199278843\/aCertificate-Request-bCertificate-Verification_Q320.jpg","link":"https:\/\/www.researchgate.net\/figure\/RO-PKI-proposed-architecture_fig1_267694127","title":"RO-PKI proposed architecture. ,"id":1637,"keyword_id":106,"url":"https:\/\/securecommunications.airbus.com\/images\/images\/1900\/13055pc PKI Building Security - L Heno-01.jpg","link":"https:\/\/securecommunications.airbus.com\/en\/meet-the-experts\/building-trusted-networks-with-pki","title":"Public Key Infrastructure is expected to support larger numbers of...","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.XoSqNhS2hXYMbffiIt0DFwHaDT&pid=15.1","size":"1900 x 849 \u00b7 jpeg","desc":"pki building trusted networks experts meet","filetype":"jpg","width":1900,"height":849,"domain":"securecommunications.airbus.com","created_at":null,"updated_at":null, Consulting Services ,"id":1639,"keyword_id":106,"url":"https:\/\/cutting-edge-cybersec.com\/pic\/architects.png","link":"https:\/\/cutting-edge-cybersec.com\/","title":"PKI Event","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.N8RO85NTz-PFizCoG5-lrAHaF4&pid=15.1","size":"642 x 510 \u00b7 png","desc":"pki","filetype":"png","width":642,"height":510,"domain":"cutting-edge-cybersec.com","created_at":null,"updated_at":null,"id":1640,"keyword_id":106,"url":"https:\/\/cdn-ak.f.st-hatena.com\/images\/fotolife\/i\/iestudy\/20191125\/20191125223016.png","link":"https:\/\/www.iestudy.work\/entry\/2019\/11\/24\/223245","title":"PKI\u306b\u3064\u3044\u3066\u6574\u7406\u3057\u307e\u3057\u305f - \u5bb6study\u3092\u3064\u3065\u3063\u3066","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.4BVtmci0vkzTHhnzcOGenwHaEX&pid=15.1","size":"494 x 291 \u00b7 png","desc":"","filetype":"png","width":494,"height":291,"domain":"www.iestudy.work","created_at":null,"updated_at":null,"id":1641,"keyword_id":106,"url":"https:\/\/www.researchgate.net\/profile\/Albert_Kwansah_Ansah\/publication\/264821916\/figure\/fig2\/AS:471850531725312@1489509341048\/Summarised-structure-of-PKI_Q320.jpg","link":"https:\/\/www.researchgate.net\/publication\/264821916_E-governance_public_key_infrastructure_PKI_model","title":"(PDF) E-governance public key infrastructure (PKI) model","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.VbeqdqkODOJQOHK0Vl9BAAAAAA&pid=15.1","size":"320 x 320 \u00b7 jpeg","desc":"pki infrastructure key governance","filetype":"jpg","width":320,"height":320,"domain":"www.researchgate.net","created_at":null,"updated_at":null,"id":1642,"keyword_id":106,"url":"https:\/\/image.slidesharecdn.com\/smartmeter-3-140402235146-phpapp02\/95\/smart-metering-infrastructure-architecture-and-analytics-6-638.jpg?cb=1400059423","link":"http:\/\/www.slideshare.net\/SandeepSharma65\/smart-meter-3","title":"Smart metering infrastructure Architecture and analytics","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.b90thJ9U_wVz-mcm37lCnwHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"metering analytics","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1643,"keyword_id":106,"url":"https:\/\/www.alleypoyner.com\/wp-content\/uploads\/2020\/06\/UNO-Peter-Kiewit-Institute_APMA_10-1024x682.jpg","link":"https:\/\/www.alleypoyner.com\/design\/peter-kiewit-institute\/","title":"Peter Kiewit Institute - Alley Poyner Macchietto Architecture","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.P2lYo7aOWB_CciGQoWJ_xQHaE7&pid=15.1","size":"1024 x 682 \u00b7 jpeg","desc":"peter institute kiewit apma omaha","filetype":"jpg","width":1024,"height":682,"domain":"www.alleypoyner.com","created_at":null,"updated_at":null,"id":1644,"keyword_id":106,"url":"https:\/\/www.precisionimages.com\/wp-content\/uploads\/2021\/02\/PKA-Entry.jpg","link":"https:\/\/www.precisionimages.com\/projects\/pka-architects\/","title":"pka Architects - Precision Images","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.iftFDeqLXfIfxASRQsTphQHaL2&pid=15.1","size":"500 x 800 \u00b7 jpeg","desc":"pka","filetype":"jpg","width":500,"height":800,"domain":"www.precisionimages.com","created_at":null,"updated_at":null,"id":1645,"keyword_id":106,"url":"http:\/\/www.fiber-optic-transceiver-module.com\/wp-content\/uploads\/2018\/08\/OpenvSwitch-architecture.jpg","link":"http:\/\/www.fiber-optic-transceiver-module.com\/openvswitch-vs-openflow-what-are-they-whats-their-relationship.html","title":"OpenvSwitch vs OpenFlow: What Are They, What's Their Relationship?","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.iMqpjoveBQ2S6dpNdShpPwHaFj&pid=15.1","size":"960 x 720 \u00b7 jpeg","desc":"openvswitch openflow architecture vs relationship optic fiber","filetype":"jpg","width":960,"height":720,"domain":"www.fiber-optic-transceiver-module.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Architecture (pdf) e-governance public key infrastructure (pki) model. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment