If you are searching about How To Create CA and Generate TLS/SSL Certificates & Keys you've came to the right page. We have 16 Pictures about How To Create CA and Generate TLS/SSL Certificates & Keys like Five Ways PKI Protects and Secures Financial Services Data | Sectigo, How PKI Works ? - RebelAdmin.com and also PPT - PUBLIC KEY ENABLING (PKE) PowerPoint Presentation, free download. Read more:
How To Create CA And Generate TLS/SSL Certificates & Keys
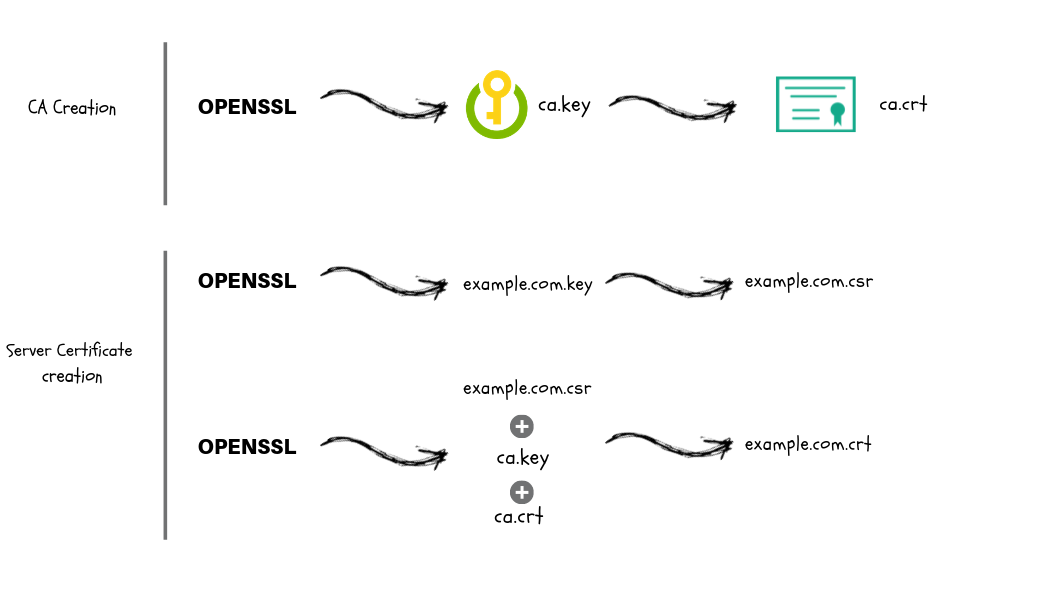 scriptcrunch.com
scriptcrunch.com tls certificates generate openssl
PKI By Tim Polk
 www.slideshare.net
www.slideshare.net pki polk
(PDF) A Survey Of PKI Components And Scalability Issues
 www.researchgate.net
www.researchgate.net pki scalability
Encryption - Is My Interpretation Of The SSL Process Correct
 cs.stackexchange.com
cs.stackexchange.com diagram process certificates does step certificate key secret master pre interpretation correct client encryption science presume comes come where
Understanding The Trusted Platform Module
 www.mayurpahwa.com
www.mayurpahwa.com module trusted platform understanding security
What Could Be Considered A Weakness Of A Digital Certificate
 digitalpicturesimg.blogspot.com
digitalpicturesimg.blogspot.com cryptography digitalpictures
366 PKI And Its Components - YouTube
 www.youtube.com
www.youtube.com pki
PPT - PUBLIC KEY ENABLING (PKE) PowerPoint Presentation, Free Download
 www.slideserve.com
www.slideserve.com key pki pke enabling presentation ppt powerpoint
Encryption Protocols: Explained | Venafi
 www.venafi.com
www.venafi.com protocols encryption venafi guest
How PKI Works ? - RebelAdmin.com
pki works process rebeladmin
Introduction To PKI Technology
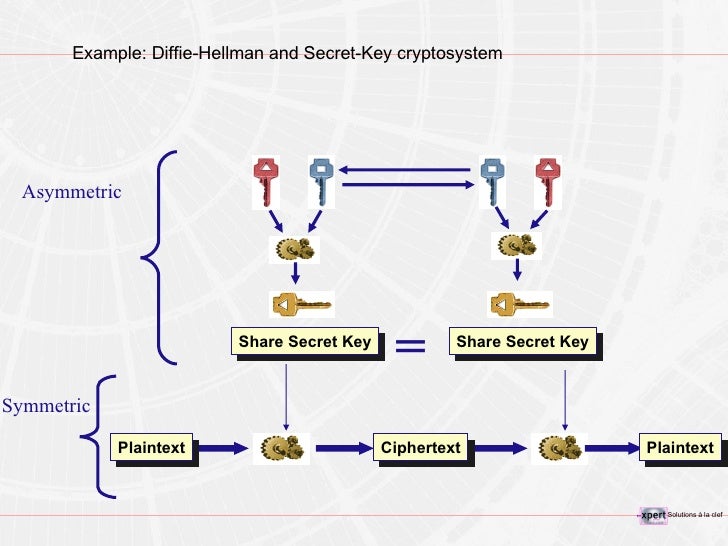 www.slideshare.net
www.slideshare.net pki
How PKI Works ? - RebelAdmin.com
pki works rebeladmin
Five Ways PKI Protects And Secures Financial Services Data | Sectigo
 sectigo.com
sectigo.com pki sectigo protects
Pki
 es.slideshare.net
es.slideshare.net pki
Cryptography Fundamentals - Infosec Resources
 resources.infosecinstitute.com
resources.infosecinstitute.com cryptography fundamentals
PKI-As-A-Service | Managed Cloud PKI Platform | PKIaaS | Encryption
 www.encryptionconsulting.com
www.encryptionconsulting.com pki lifecycle migration encryptionconsulting
How pki works ?. How to create ca and generate tls/ssl certificates & keys. Pki lifecycle migration encryptionconsulting
if you are looking "id":112,"keyword_id":2,"name":"PKI Explained","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1768,"keyword_id":112,"url":"https:\/\/sectigo.com\/uploads\/audio\/_1200x630_crop_center-center_82_none\/PKI-in-FinSvcs-Diagram-LI-FINAL.png","link":"https:\/\/sectigo.com\/blog\/five-ways-pki-protects-and-secures-financial-services-data","title":"Five Ways PKI Protects and Secures Financial Services Data ,"id":1769,"keyword_id":112,"url":"http:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/pki6.png","link":"https:\/\/www.rebeladmin.com\/2018\/05\/how-pki-works\/","title":"How PKI Works ? - RebelAdmin.com","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.O0rojEYpa8moff6jtAx-EgHaDc&pid=15.1","size":"924 x 429 \u00b7 png","desc":"pki works process rebeladmin","filetype":"png","width":924,"height":429,"domain":"www.rebeladmin.com","created_at":null,"updated_at":null,"id":1770,"keyword_id":112,"url":"https:\/\/cdn.slidesharecdn.com\/ss_thumbnails\/pki-130927173621-phpapp02-thumbnail-4.jpg?cb=1380303618","link":"https:\/\/es.slideshare.net\/MiriamMedinaTapia\/pki-26632378","title":"Pki","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.hYYdWD0Z8cUtoHY44bABegHaFj&pid=15.1","size":"768 x 576 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":768,"height":576,"domain":"es.slideshare.net","created_at":null,"updated_at":null,"id":1771,"keyword_id":112,"url":"https:\/\/image1.slideserve.com\/3355219\/what-is-pki-l.jpg","link":"https:\/\/www.slideserve.com\/foy\/public-key-enabling-pke","title":"PPT - PUBLIC KEY ENABLING (PKE) PowerPoint Presentation, free download","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.X-FjRJfEa2YcT5qwEJO_2gHaFj&pid=15.1","size":"1024 x 768 \u00b7 jpeg","desc":"key pki pke enabling presentation ppt powerpoint","filetype":"jpg","width":1024,"height":768,"domain":"www.slideserve.com","created_at":null,"updated_at":null,"id":1772,"keyword_id":112,"url":"https:\/\/i.ytimg.com\/vi\/PsuHXtF6tqg\/hqdefault.jpg","link":"https:\/\/www.youtube.com\/watch?v=PsuHXtF6tqg","title":"366 PKI and Its Components - YouTube","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.8KSAVWocNoTwZEmKJ2QLJwHaFj&pid=15.1","size":"480 x 360 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":480,"height":360,"domain":"www.youtube.com","created_at":null,"updated_at":null,"id":1773,"keyword_id":112,"url":"http:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/pki1.png","link":"http:\/\/www.rebeladmin.com\/2018\/05\/how-pki-works\/","title":"How PKI Works ? - RebelAdmin.com","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.eH4lv2ct3i7ucoziGmd2ZAAAAA&pid=15.1","size":"286 x 279 \u00b7 png","desc":"pki works rebeladmin","filetype":"png","width":286,"height":279,"domain":"www.rebeladmin.com","created_at":null,"updated_at":null,"id":1774,"keyword_id":112,"url":"https:\/\/scriptcrunch.com\/wp-content\/uploads\/2018\/11\/openssl-1.png","link":"https:\/\/scriptcrunch.com\/create-ca-tls-ssl-certificates-keys\/","title":"How To Create CA and Generate TLS\/SSL Certificates & Keys","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.BUludnazJwx_oQ69g4Vb3QHaEM&pid=15.1","size":"1060 x 600 \u00b7 png","desc":"tls certificates generate openssl","filetype":"png","width":1060,"height":600,"domain":"scriptcrunch.com","created_at":null,"updated_at":null,"id":1775,"keyword_id":112,"url":"https:\/\/www.researchgate.net\/profile\/William-Yurcik\/publication\/220780872\/figure\/fig1\/AS:305401691164672@1449824845766\/figure-fig1_Q320.jpg","link":"https:\/\/www.researchgate.net\/publication\/220780872_A_survey_of_PKI_components_and_scalability_issues","title":"(PDF) A survey of PKI components and scalability issues","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.UYtC0shYtLBzrbBcGajQVQAAAA&pid=15.1","size":"316 x 316 \u00b7 jpeg","desc":"pki scalability","filetype":"jpg","width":316,"height":316,"domain":"www.researchgate.net","created_at":null,"updated_at":null,"id":1776,"keyword_id":112,"url":"https:\/\/image.slidesharecdn.com\/introductiontopkitechnology-090502145056-phpapp02\/95\/introduction-to-pki-technology-93-728.jpg?cb=1241276083","link":"https:\/\/www.slideshare.net\/smaret\/introduction-to-pki-technology","title":"Introduction To PKI Technology","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.L85MVneuJet-l9-PvlKhRgHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1777,"keyword_id":112,"url":"https:\/\/i.stack.imgur.com\/Vgww8.gif","link":"https:\/\/cs.stackexchange.com\/questions\/65260\/is-my-interpretation-of-the-ssl-process-correct","title":"encryption - Is my interpretation of the SSL process correct","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.X_1z5WGqjcyWjBS4BQaEGQHaFi&pid=15.1","size":"700 x 524 \u00b7 gif","desc":"diagram process certificates does step certificate key secret master pre interpretation correct client encryption science presume comes come where","filetype":"gif","width":700,"height":524,"domain":"cs.stackexchange.com","created_at":null,"updated_at":null,"id":1778,"keyword_id":112,"url":"https:\/\/www.encryptionconsulting.com\/wp-content\/uploads\/2020\/05\/root-CA.jpg","link":"https:\/\/www.encryptionconsulting.com\/pki-as-a-service\/","title":"PKI-As-A-Service ,"id":1779,"keyword_id":112,"url":"https:\/\/image.slidesharecdn.com\/polk-140303204910-phpapp02\/95\/pki-by-tim-polk-19-638.jpg?cb=1393879767","link":"https:\/\/www.slideshare.net\/natemiller67\/pki-by-tim-polk","title":"PKI by Tim Polk","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.l8DEaN2f9oNyeqQjg-duWQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki polk","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1780,"keyword_id":112,"url":"https:\/\/1.bp.blogspot.com\/-85GxmB8yGoQ\/XpxUcIITCZI\/AAAAAAAACkc\/RLZNAkPQMwsmnxC13jBCZEAjeGUYfK_rACNcBGAsYHQ\/s1600\/cyber-2377718_1280.jpg","link":"https:\/\/www.mayurpahwa.com\/2020\/04\/understanding-trusted-platform-module.html","title":"Understanding the Trusted Platform Module","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.SEW_-22ciqG8IcKkXbPbdgHaE9&pid=15.1","size":"1280 x 858 \u00b7 jpeg","desc":"module trusted platform understanding security","filetype":"jpg","width":1280,"height":858,"domain":"www.mayurpahwa.com","created_at":null,"updated_at":null, Venafi","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.2eAt224xWqGllvJ-bKy12QHaCA&pid=15.1","size":"1200 x 325 \u00b7 png","desc":"protocols encryption venafi guest","filetype":"png","width":1200,"height":325,"domain":"www.venafi.com","created_at":null,"updated_at":null,"id":1782,"keyword_id":112,"url":"https:\/\/image.slidesharecdn.com\/introtocryptographyfinal-170815123246\/95\/introduction-to-cryptography-and-the-public-key-infrastructure-1-638.jpg?cb=1502800661","link":"https:\/\/digitalpicturesimg.blogspot.com\/2020\/03\/what-could-be-considered-weakness-of.html","title":"What Could Be Considered A Weakness Of A Digital Certificate","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.FqdoEFArkP7YpdmAfZf-uwHaJl&pid=15.1","size":"638 x 826 \u00b7 jpeg","desc":"cryptography digitalpictures","filetype":"jpg","width":638,"height":826,"domain":"digitalpicturesimg.blogspot.com","created_at":null,"updated_at":null,"id":1783,"keyword_id":112,"url":"https:\/\/mk0resourcesinf5fwsf.kinstacdn.com\/wp-content\/uploads\/2020\/10\/cryptography_fundamentals-2.png","link":"https:\/\/resources.infosecinstitute.com\/topic\/cryptography-fundamentals\/","title":"Cryptography Fundamentals - Infosec Resources","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.o5XIHU5ZrXIksMiHtMEXzwHaJl&pid=15.1","size":"1289 x 1668 \u00b7 png","desc":"cryptography fundamentals","filetype":"png","width":1289,"height":1668,"domain":"resources.infosecinstitute.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Explained (pdf) a survey of pki components and scalability issues. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment