If you are searching about What Is PKI (Public Key Infrastructure) you've came to the right page. We have 16 Pics about What Is PKI (Public Key Infrastructure) like How PKI Works ? - Technical Blog | REBELADMIN, pki | Encryption Consulting and also Expired Certificate Allows Data Exfiltration | Venafi. Here you go:
What Is PKI (Public Key Infrastructure)
pki infrastructure key flow process introduction
Pki | Encryption Consulting
 www.encryptionconsulting.com
www.encryptionconsulting.com pki kgb encryption
The Internet Overview An Introduction To
 present5.com
present5.com CS200: Notes 16 April 2004
rsa algorithm encryption crypto cs200 afraid feds america regeneration cs virginia edu ciphertext decryption
Gartner's Magic Quadrant For User Authentication
 www.gemalto.com
www.gemalto.com gartner quadrant authentication gemalto 2fa
What Is Cryptolocker And How To Protect Yourself – The Security Blogger
cryptolocker key private protect yourself
Expired Certificate Allows Data Exfiltration | Venafi
 www.venafi.com
www.venafi.com certificate expired allowed venafi exfiltration gao extended report data
Google Blocked Unauthorized Digital Certificates IssuedSecurity Affairs
digital pki certificate key infrastructure certificates signature blocked unauthorized nic india securityaffairs class implementations
How PKI Works ? - Technical Blog | REBELADMIN
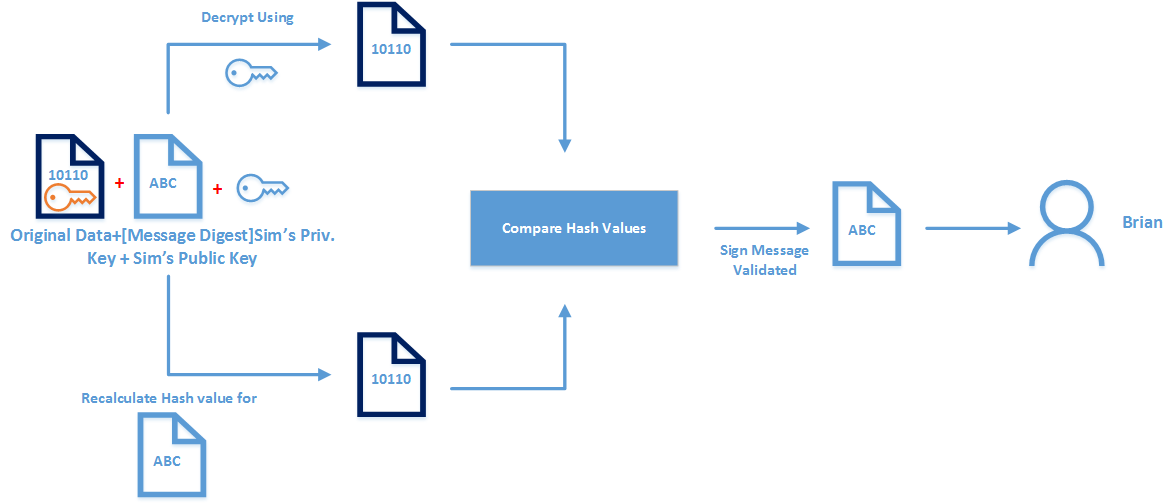 www.rebeladmin.com
www.rebeladmin.com pki works process explained key rebeladmin messages encryption verification signature decrypt decryption
Overall Cryptography And Pki Introduction
 www.slideshare.net
www.slideshare.net cryptography pki overall
Cryptography And PKI
 www.slideshare.net
www.slideshare.net cryptography pki
5 Ways Automation Improve Machine Identity Protection | Venafi
 www.venafi.com
www.venafi.com trading venafi machine automation identity protection ways apps improves undervalued identities yet again improve management
PKI And Applications
 www.slideshare.net
www.slideshare.net pki
3 Steps To Implementing Your Public Key Infrastructure (PKI
 www.tevora.com
www.tevora.com pki implementing
5 Cryptography Part2
 www.slideshare.net
www.slideshare.net cryptography part2
How To Choose A PKI Service Provider
 www.stayful.com
www.stayful.com pki
Cs200: notes 16 april 2004. Pki kgb encryption. Certificate expired allowed venafi exfiltration gao extended report data
if you are looking "id":104,"keyword_id":2,"name":"PKI Encryption","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":[ REBELADMIN","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.O7g9GSazwgdj2TKD_rv3cgHaDL&pid=15.1","size":"1173 x 504 \u00b7 png","desc":"pki works process explained key rebeladmin messages encryption verification signature decrypt decryption","filetype":"png","width":1173,"height":504,"domain":"www.rebeladmin.com","created_at":null,"updated_at":null,"id":1578,"keyword_id":104,"url":"https:\/\/www.encryptionconsulting.com\/wp-content\/uploads\/2021\/03\/pki-600x391.jpg","link":"https:\/\/www.encryptionconsulting.com\/pki\/","title":"pki ,"id":1579,"keyword_id":104,"url":"http:\/\/www.thesecurityblogger.com\/wp-content\/uploads\/2013\/12\/assemcrypto.gif","link":"http:\/\/thesecurityblogger.com\/?p=3421","title":"What is Cryptolocker and how to protect yourself \u2013 The Security Blogger","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.6YsGlwQvQu8gSjFHF9-2wQAAAA&pid=15.1","size":"434 x 297 \u00b7 png","desc":"cryptolocker key private protect yourself","filetype":"png","width":434,"height":297,"domain":"thesecurityblogger.com","created_at":null,"updated_at":null,"id":1580,"keyword_id":104,"url":"https:\/\/www.tevora.com\/wp-content\/uploads\/2017\/09\/data-encryption.jpeg","link":"http:\/\/www.tevora.com\/3-steps-implementing-public-key-infrastructure-pki-architecture\/","title":"3 Steps to Implementing Your Public Key Infrastructure (PKI","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.UV1Iamm6zGyTjwY3Q4tMPwHaE7&pid=15.1","size":"2048 x 1365 \u00b7 jpeg","desc":"pki implementing","filetype":"jpg","width":2048,"height":1365,"domain":"www.tevora.com","created_at":null,"updated_at":null,"id":1581,"keyword_id":104,"url":"http:\/\/www.herongyang.com\/PKI\/PKI_Introduction.jpg","link":"http:\/\/www.herongyang.com\/PKI\/Introduction-What-Is-PKI-Public-Key-Infrastructure.html","title":"What Is PKI (Public Key Infrastructure)","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.dVAiEXBhg_-GgdgyS6VW4AHaFL&pid=15.1","size":"427 x 299 \u00b7 jpeg","desc":"pki infrastructure key flow process introduction","filetype":"jpg","width":427,"height":299,"domain":"www.herongyang.com","created_at":null,"updated_at":null,"id":1582,"keyword_id":104,"url":"https:\/\/www.stayful.com\/wp-content\/uploads\/2021\/06\/Encryption-540x371.png","link":"https:\/\/www.stayful.com\/business\/how-to-choose-a-pki-service-provider\/","title":"How To Choose A PKI Service Provider","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.BafrdGFNBAbmi07OrNonyQHaFF&pid=15.1","size":"540 x 371 \u00b7 png","desc":"pki","filetype":"png","width":540,"height":371,"domain":"www.stayful.com","created_at":null,"updated_at":null,"id":1583,"keyword_id":104,"url":"https:\/\/image.slidesharecdn.com\/pkiandapplications-1213824493775384-9\/95\/pki-and-applications-8-728.jpg?cb=1213799136","link":"https:\/\/www.slideshare.net\/nakov\/pki-and-applications","title":"PKI and Applications","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.8cuNtE9NFkn30ZWz1WBjXwHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1584,"keyword_id":104,"url":"https:\/\/image.slidesharecdn.com\/overallcryptographyandpkiupdate-121009014046-phpapp02\/95\/overall-cryptography-and-pki-introduction-25-728.jpg?cb=1349746915","link":"https:\/\/www.slideshare.net\/mita29\/overall-cryptography-and-pki-introduction","title":"Overall cryptography and pki introduction","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.4CZnIgHzzueyeZ76L_pclAHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"cryptography pki overall","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1585,"keyword_id":104,"url":"https:\/\/image.slidesharecdn.com\/cryptographyandpki-161203173839\/95\/cryptography-and-pki-17-638.jpg?cb=1480786779","link":"https:\/\/www.slideshare.net\/RabeiAli1\/cryptography-and-pki-69792073","title":"Cryptography and PKI","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.P4tcO2FKfcY4AVbzZ7dpCgHaEK&pid=15.1","size":"638 x 359 \u00b7 jpeg","desc":"cryptography pki","filetype":"jpg","width":638,"height":359,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1586,"keyword_id":104,"url":"http:\/\/securityaffairs.co\/wordpress\/wp-content\/uploads\/2014\/07\/digital-certificate-picture.png","link":"http:\/\/securityaffairs.co\/wordpress\/26495\/cyber-crime\/blocked-digital-certificates-nic-india.html","title":"Google blocked unauthorized digital certificates issuedSecurity Affairs","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.aTJFZm9Bzo-DxdANH-GyJgHaES&pid=15.1","size":"971 x 563 \u00b7 png","desc":"digital pki certificate key infrastructure certificates signature blocked unauthorized nic india securityaffairs class implementations","filetype":"png","width":971,"height":563,"domain":"securityaffairs.co","created_at":null,"updated_at":null,"id":1587,"keyword_id":104,"url":"https:\/\/image.slidesharecdn.com\/5cryptographypart2-13308987657859-phpapp01-120304160705-phpapp01\/85\/5-cryptography-part2-19-320.jpg?cb=1330877312","link":"https:\/\/www.slideshare.net\/aouyang\/5-cryptography-part2-11860062","title":"5 Cryptography Part2","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.yqvOkB09mgTw6GbGTwbo7gAAAA&pid=15.1","size":"320 x 240 \u00b7 jpeg","desc":"cryptography part2","filetype":"jpg","width":320,"height":240,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1588,"keyword_id":104,"url":"https:\/\/www.gemalto.com\/press-site\/PublishingImages\/2014-December-Gartner-Magic-Quadrant.jpg","link":"http:\/\/www.gemalto.com\/companyinfo\/media\/gartner-magic-quadrant-for-user-authentication","title":"Gartner's Magic Quadrant for User Authentication","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.8uE0kP7JaFW0Vjw0UC1llAHaHu&pid=15.1","size":"598 x 624 \u00b7 jpeg","desc":"gartner quadrant authentication gemalto 2fa","filetype":"jpg","width":598,"height":624,"domain":"www.gemalto.com","created_at":null,"updated_at":null, Venafi","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.foItEIuo9viiqIx-m36xTgHaCA&pid=15.1","size":"1200 x 325 \u00b7 jpeg","desc":"trading venafi machine automation identity protection ways apps improves undervalued identities yet again improve management","filetype":"jpg","width":1200,"height":325,"domain":"www.venafi.com","created_at":null,"updated_at":null, Venafi","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.-k30GVs-qx47zVbLKvwVQQHaCA&pid=15.1","size":"1200 x 325 \u00b7 jpeg","desc":"certificate expired allowed venafi exfiltration gao extended report data","filetype":"jpg","width":1200,"height":325,"domain":"www.venafi.com","created_at":null,"updated_at":null,"id":1591,"keyword_id":104,"url":"http:\/\/www.cs.virginia.edu\/cs200\/lectures\/rsa.jpg","link":"http:\/\/www.cs.virginia.edu\/cs200\/lectures\/notes36.html","title":"CS200: Notes 16 April 2004","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.lDSUwioz4drxet6j4AhU7gHaGa&pid=15.1","size":"688 x 596 \u00b7 jpeg","desc":"rsa algorithm encryption crypto cs200 afraid feds america regeneration cs virginia edu ciphertext decryption","filetype":"jpg","width":688,"height":596,"domain":"www.cs.virginia.edu","created_at":null,"updated_at":null,"id":1592,"keyword_id":104,"url":"https:\/\/present5.com\/presentation\/534fb19deda8d661a65743880572bcb7\/image-123.jpg","link":"https:\/\/present5.com\/the-internet-overview-an-introduction-to\/","title":"The Internet Overview An introduction to","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.9E0lH5-xQ_1BAbjebhMneQHaFj&pid=15.1","size":"720 x 540 \u00b7 jpeg","desc":"","filetype":"jpg","width":720,"height":540,"domain":"present5.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Encryption Expired certificate allows data exfiltration. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment