If you are looking for Two-Tier PKI Hierarchy – Part 1 – Root Certification Authority you've came to the right page. We have 16 Images about Two-Tier PKI Hierarchy – Part 1 – Root Certification Authority like Understanding Certificates and PKI - Technical Documentation - Support, PKI-As-A-Service | Managed Cloud PKI Platform | PKIaaS | Encryption and also Understanding Certificates and PKI - Technical Documentation - Support. Read more:
Two-Tier PKI Hierarchy – Part 1 – Root Certification Authority
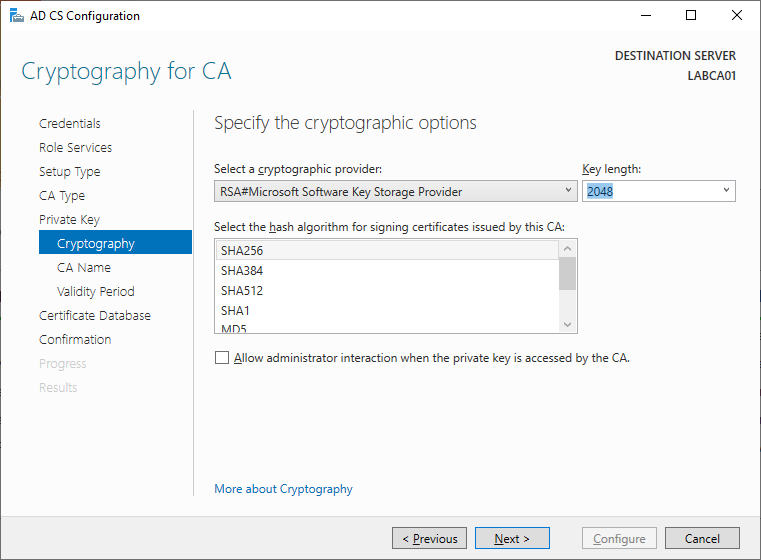 blog.naglis.no
blog.naglis.no pki specify
Overall Cryptography And Pki Introduction
 www.slideshare.net
www.slideshare.net pki cryptography
Two-Tier PKI Hierarchy – Part 1 – Root Certification Authority
 blog.naglis.no
blog.naglis.no pki tier hierarchy
Basic Concept Of Pki
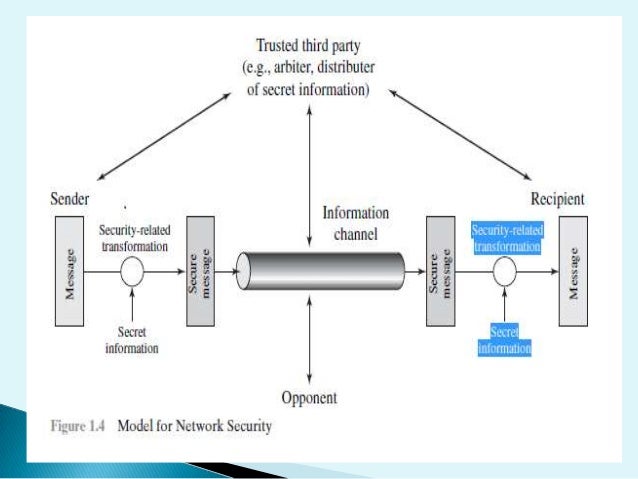 www.slideshare.net
www.slideshare.net pki
Active Directory Certificate Service | RebelAdmin.com
pki certificate highly secure properties process directory active rebeladmin hierarchy devices microsoft seven ca3
PKI-As-A-Service | Managed Cloud PKI Platform | PKIaaS | Encryption
 www.encryptionconsulting.com
www.encryptionconsulting.com pki encryption hierarchy
Microsoft PKI Services | Design And Deployment Services | RNTrust
 www.rntrust.ae
www.rntrust.ae pki
Etibar Taghiyev's Blog: BGP Security
 etibartaghiyev.blogspot.com
etibartaghiyev.blogspot.com bgp security pki hierarchy figure
Certificates - What Web Browsers Support OCSP Stapling? Are The Privacy
 security.stackexchange.com
security.stackexchange.com ocsp web stapling browsers privacy performance support pki same features source stack
PKI Hierarchy - YouTube
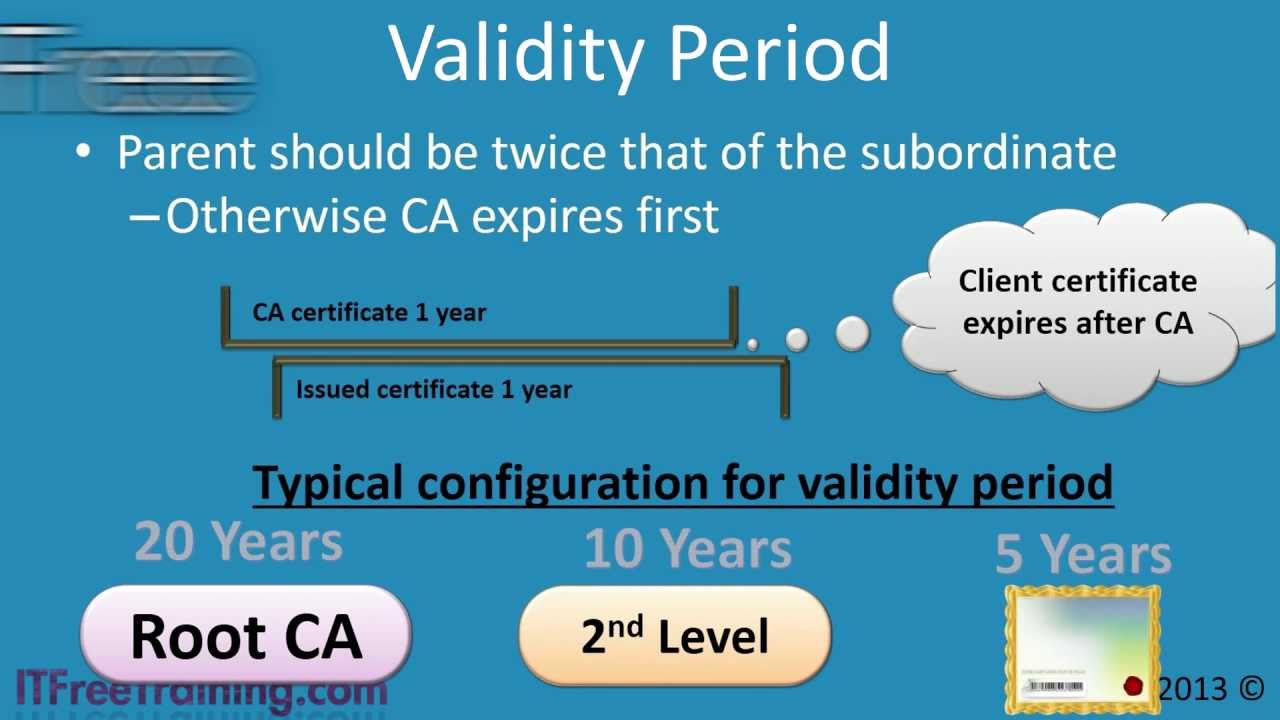 www.youtube.com
www.youtube.com pki hierarchy
PKI Interoperability Models (February 2005) - 4.1. Root CA/Hierarchy Model
pki hierarchy interoperability models 2005 figure structure root february mesh
Summary Of Protocols For PKI Interoperability
 www.entrust.com
www.entrust.com pki summary interoperability protocols component brief purpose each entrust
How Certificate Chains Work
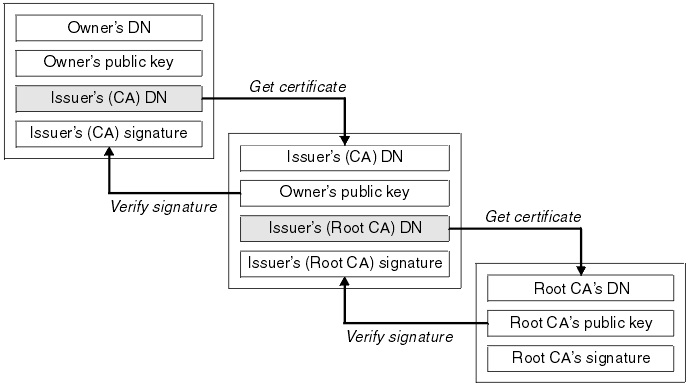 knowledge.digicert.com
knowledge.digicert.com certificate hierarchy chain trust root certificates path chains certification digicert intermediate solution order pki begins owner illustration where
Understanding Certificates And PKI - Technical Documentation - Support
pki hierarchy trust certificates understanding certificate juniper domain documentation figure
Pki Diagram
 bishosoft.com
bishosoft.com pki diagram
PKI: CA階層, 2/3 Tierと基礎 | Netsphere Laboratories
Two-tier pki hierarchy – part 1 – root certification authority. How certificate chains work. Overall cryptography and pki introduction
if you are looking "id":111,"keyword_id":2,"name":"PKI Hierarchy","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1711,"keyword_id":111,"url":"http:\/\/www.juniper.net\/techpubs\/images\/g030622.gif","link":"http:\/\/www.juniper.net\/documentation\/en_US\/junos\/topics\/concept\/certificate-digital-understanding.html","title":"Understanding Certificates and PKI - Technical Documentation - Support","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.TJm0AgO9MhzXM0PZOG-8sQHaFT&pid=15.1","size":"885 x 633 \u00b7 gif","desc":"pki hierarchy trust certificates understanding certificate juniper domain documentation figure","filetype":"gif","width":885,"height":633,"domain":"www.juniper.net","created_at":null,"updated_at":null, PKIaaS ,"id":1713,"keyword_id":111,"url":"http:\/\/www.rebeladmin.com\/wp-content\/uploads\/2018\/05\/ca3.png","link":"http:\/\/www.rebeladmin.com\/tag\/active-directory-certificate-service\/","title":"Active Directory Certificate Service , Design and Deployment Services ,"id":1715,"keyword_id":111,"url":"http:\/\/www.galexia.com\/public\/research\/assets\/pki_interoperability_models_2005\/pki_interoperability_models_200500001.png","link":"http:\/\/www.galexia.com\/public\/research\/assets\/pki_interoperability_models_2005\/pki_interoperability_models_2005-4_1_.html","title":"PKI Interoperability Models (February 2005) - 4.1. Root CA\/Hierarchy Model","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.X7YChljeIJ0eNeY2CKgBwAHaHV&pid=15.1","size":"517 x 512 \u00b7 png","desc":"pki hierarchy interoperability models 2005 figure structure root february mesh","filetype":"png","width":517,"height":512,"domain":"www.galexia.com","created_at":null,"updated_at":null,"id":1716,"keyword_id":111,"url":"https:\/\/www.entrust.com\/-\/media\/entrust\/resources\/product-support\/certificate-solutions\/managedpki.gif?la=en&hash=2162166F1AE7DDF23B5BF6CDFDAB7B6C","link":"https:\/\/www.entrust.com\/resources\/certificate-solutions\/learn\/summary-of-protocols-for-pki-interoperability","title":"Summary of Protocols for PKI Interoperability","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.ny2hOu37ohdTioUq2S18bQAAAA&pid=15.1","size":"418 x 246 \u00b7 gif","desc":"pki summary interoperability protocols component brief purpose each entrust","filetype":"gif","width":418,"height":246,"domain":"www.entrust.com","created_at":null,"updated_at":null,"id":1717,"keyword_id":111,"url":"https:\/\/2.bp.blogspot.com\/-kGQ_NLC0EeM\/ThtdWseksAI\/AAAAAAAAACk\/zruX-pL2i30\/s320\/BGP-PKI.png","link":"https:\/\/etibartaghiyev.blogspot.com\/2011\/07\/bgp-security.html","title":"Etibar Taghiyev's Blog: BGP Security","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.NWaTLcEOn-HfLho1Yqne-wAAAA&pid=15.1","size":"320 x 198 \u00b7 png","desc":"bgp security pki hierarchy figure","filetype":"png","width":320,"height":198,"domain":"etibartaghiyev.blogspot.com","created_at":null,"updated_at":null,"id":1718,"keyword_id":111,"url":"https:\/\/i.stack.imgur.com\/T0ESx.gif","link":"https:\/\/security.stackexchange.com\/questions\/12735\/what-web-browsers-support-ocsp-stapling-are-the-privacy-and-performance-feature","title":"certificates - What web browsers support OCSP stapling? Are the privacy","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.Dl0e-yrFOd6RmIc3nNs30AAAAA&pid=15.1","size":"434 x 253 \u00b7 gif","desc":"ocsp web stapling browsers privacy performance support pki same features source stack","filetype":"gif","width":434,"height":253,"domain":"security.stackexchange.com","created_at":null,"updated_at":null,"id":1719,"keyword_id":111,"url":"http:\/\/bp0.blogger.com\/_2xduua7nmyw\/SIUoRSXs5bI\/AAAAAAAAAQg\/C49rqGDuoro\/s400\/Figure%2B2%2B-%2BStandard%2BPKI%2BInfrastructure.jpg","link":"http:\/\/bishosoft.com\/js\/pki-diagram","title":"Pki Diagram","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.h_qT7QNndLn-lRfoigqCnwAAAA&pid=15.1","size":"400 x 325 \u00b7 jpeg","desc":"pki diagram","filetype":"jpg","width":400,"height":325,"domain":"bishosoft.com","created_at":null,"updated_at":null,"id":1720,"keyword_id":111,"url":"https:\/\/blog.naglis.no\/wp-content\/uploads\/2020\/04\/PKI16.png","link":"https:\/\/blog.naglis.no\/?p=3121","title":"Two-Tier PKI Hierarchy \u2013 Part 1 \u2013 Root Certification Authority","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.Lm7ZguTLezQeC7KaED2LTwHaFc&pid=15.1","size":"761 x 560 \u00b7 png","desc":"pki specify","filetype":"png","width":761,"height":560,"domain":"blog.naglis.no","created_at":null,"updated_at":null,"id":1721,"keyword_id":111,"url":"https:\/\/i.ytimg.com\/vi\/n_2RvlSpWEU\/maxresdefault.jpg","link":"https:\/\/www.youtube.com\/watch?v=n_2RvlSpWEU","title":"PKI Hierarchy - YouTube","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.1RWFiuTALTc_sthFmEGdOQHaEK&pid=15.1","size":"1280 x 720 \u00b7 jpeg","desc":"pki hierarchy","filetype":"jpg","width":1280,"height":720,"domain":"www.youtube.com","created_at":null,"updated_at":null,"id":1722,"keyword_id":111,"url":"https:\/\/blog.naglis.no\/wp-content\/uploads\/2020\/04\/PKI5.png","link":"https:\/\/blog.naglis.no\/?p=3121","title":"Two-Tier PKI Hierarchy \u2013 Part 1 \u2013 Root Certification Authority","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.vmjrLDF6u27oniYqxmIbUQAAAA&pid=15.1","size":"416 x 436 \u00b7 png","desc":"pki tier hierarchy","filetype":"png","width":416,"height":436,"domain":"blog.naglis.no","created_at":null,"updated_at":null,"id":1723,"keyword_id":111,"url":"http:\/\/www.nslabs.jp\/pki\/3tier-ca-hierarchy.png","link":"http:\/\/www.nslabs.jp\/pki-ca-hierarchy-and-basics.rhtml","title":"PKI: CA\u968e\u5c64, 2\/3 tier\u3068\u57fa\u790e ,"id":1724,"keyword_id":111,"url":"https:\/\/image.slidesharecdn.com\/basicconceptofpki-130426145529-phpapp01\/95\/basic-concept-of-pki-6-638.jpg?cb=1366988166","link":"https:\/\/www.slideshare.net\/PrabhatGoel1\/basic-concept-of-pki","title":"Basic concept of pki","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.DG5t_Eyz8X4u4mO7HKLZoQHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"pki","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1725,"keyword_id":111,"url":"https:\/\/image.slidesharecdn.com\/overallcryptographyandpkiupdate-121009014046-phpapp02\/95\/overall-cryptography-and-pki-introduction-12-728.jpg?cb=1349746915","link":"https:\/\/www.slideshare.net\/mita29\/overall-cryptography-and-pki-introduction","title":"Overall cryptography and pki introduction","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.KGGmSFvCpQViAEw1JydEbAHaFj&pid=15.1","size":"728 x 546 \u00b7 jpeg","desc":"pki cryptography","filetype":"jpg","width":728,"height":546,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1726,"keyword_id":111,"url":"https:\/\/knowledge.digicert.com\/content\/dam\/digicertknowledgebase\/library\/VERISIGN\/ALL_OTHER\/Eduardo\/Figure_Chain.jpg","link":"https:\/\/knowledge.digicert.com\/solution\/SO16297.html","title":"How Certificate Chains Work","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.Ai9QpKhfoK2C-x5OtnMw1gHaEJ&pid=15.1","size":"690 x 387 \u00b7 jpeg","desc":"certificate hierarchy chain trust root certificates path chains certification digicert intermediate solution order pki begins owner illustration where","filetype":"jpg","width":690,"height":387,"domain":"knowledge.digicert.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about PKI Hierarchy Microsoft pki services. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment