If you are looking for Nexus GO PKI Card layouts and technology - - Nexus Documentation you've visit to the right page. We have 17 Images about Nexus GO PKI Card layouts and technology - - Nexus Documentation like User Authentication Through the Use of Public Key Infrastructure (PKI, Smart Card Authentication and also Nexus GO PKI Card layouts and technology - - Nexus Documentation. Read more:
Nexus GO PKI Card Layouts And Technology - - Nexus Documentation
User Authentication Through The Use Of Public Key Infrastructure (PKI
pki key infrastructure authentication user through certificate dimitri meacham contributed robert
HHS ID Badge Smart Card
 ocio.nih.gov
ocio.nih.gov card smart computer smartcard built reader laptop piv slot nih badge
Enabling Smart Card Support
 docs.centrify.com
docs.centrify.com pkcs smart card centrify module enabling support path complete
Smart Cards And Biometrics: Your Key To PKI | Linux Journal
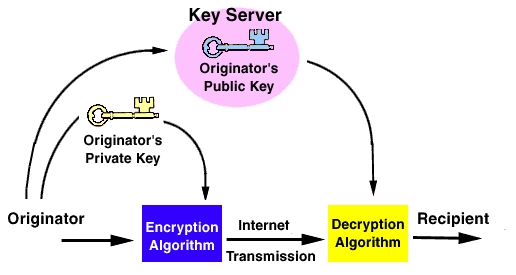 www.linuxjournal.com
www.linuxjournal.com biometrics key linuxjournal pki smart cards receiver figure
Fred's Integration Blog
 another-soa-blog.blogspot.com
another-soa-blog.blogspot.com pki certificate fred integration usage figure
Certificate Hierarchy – Certificates Templates Free
certificate hierarchy chain trust root certificates path chains certification digicert order solution pki admin february january
Smart Card Authentication
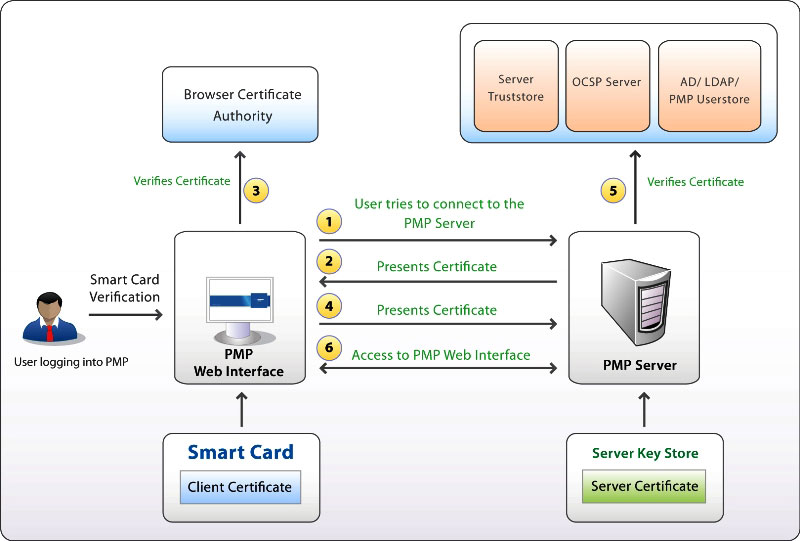 www.manageengine.com
www.manageengine.com authentication smart card process smartcard server password user access enabling web manager interface
ActivID® ActivKey USB Tokens – Two Factor Authentication - HID Global
usb hid tokens activid token pki authentication specifications overview hidglobal factor
Personal E-ID Cards In Hungary | Microsec.com - /en/pki-blog/personal-e
 www.microsec.hu
www.microsec.hu hungary cards personal card electronic identification
FIDO, PKI & Beyond: Where Authentication Meets Identification
 www.slideshare.net
www.slideshare.net fido pki authentication ctbc
How To Use PKNIC Prepaid Card? | DoctorHoster - Blog
 doctorhoster.com
doctorhoster.com prepaid billing
Using Tokens/Smartcards (PKCS#11) - SparkLabs
pkcs using smartcards sparklabs tokens
ΣΥΖΕΥΞΙΣ και PKI | ΣΥΖΕΥΞΙΣ
PIV Overview
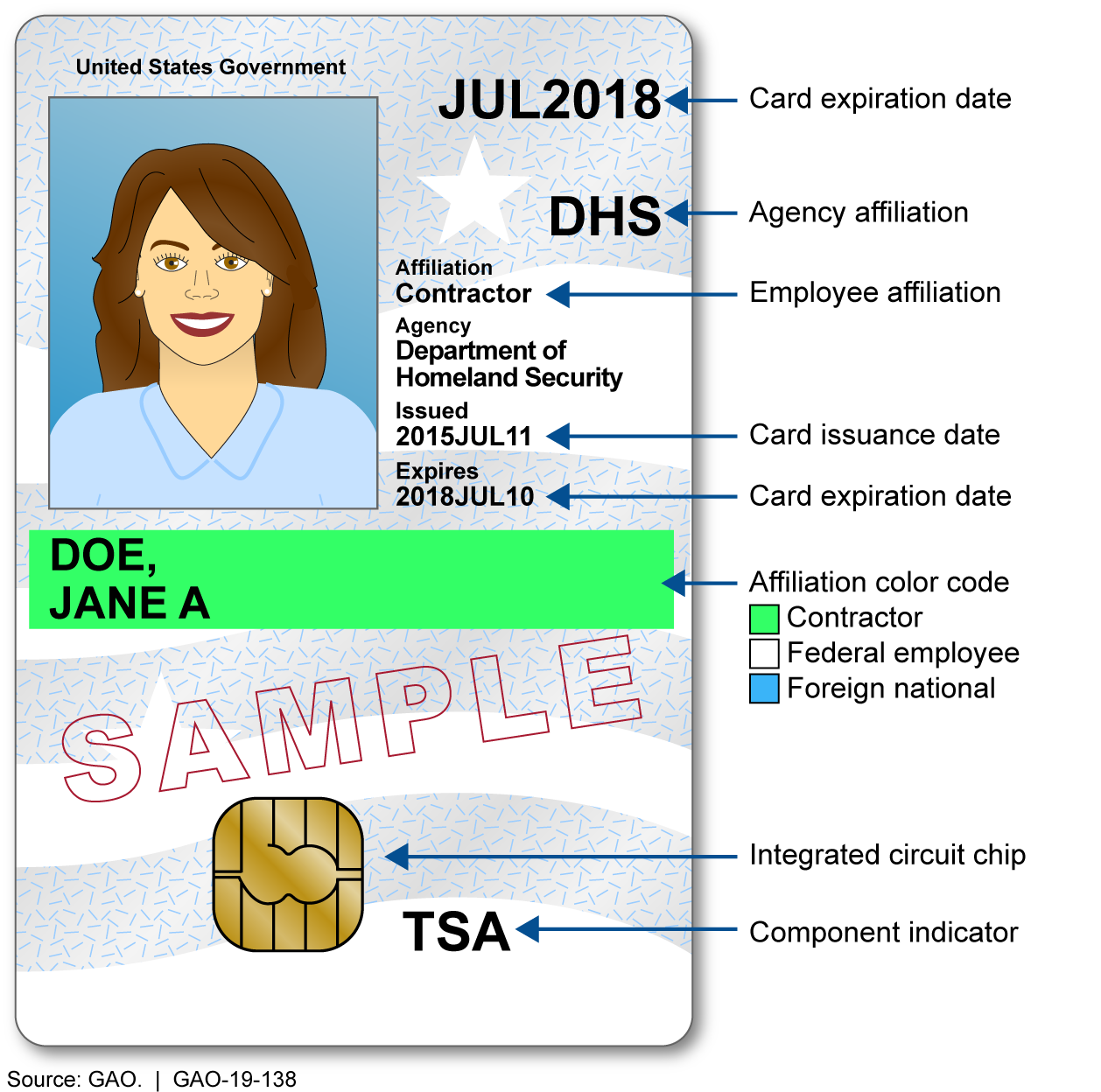 playbooks.idmanagement.gov
playbooks.idmanagement.gov piv overview
EIDAuthenticate - Smart Card Authentication On Stand Alone Computers
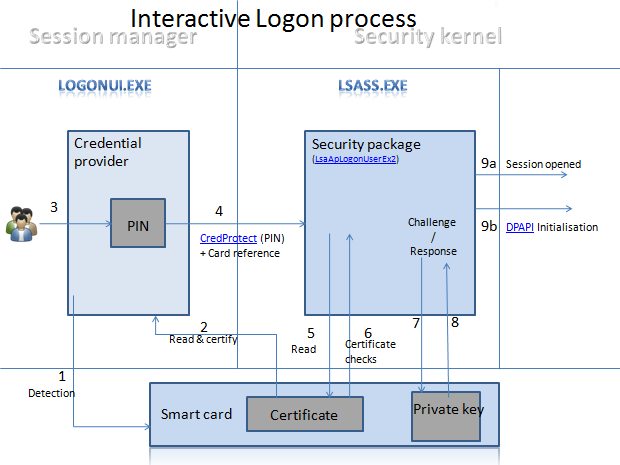 www.mysmartlogon.com
www.mysmartlogon.com card smart authentication logon process computers alone stand
PKI And Application Access
pki breach
Hhs id badge smart card. Hungary cards personal card electronic identification. Fido, pki & beyond: where authentication meets identification
if you are looking "id":76,"keyword_id":2,"name":"pki card","scraped_at":"2022-10-01 03:08:02","created_at":"2022-10-01T03:08:02.000000Z","updated_at":"2022-10-01T03:08:02.000000Z","images":["id":1148,"keyword_id":76,"url":"http:\/\/infosecwriters.com\/sites\/default\/files\/styles\/article_image_full_node\/public\/field\/image\/PKI-Certificate.gif?itok=wT5acsOe","link":"http:\/\/infosecwriters.com\/articles\/2015\/11\/25\/user-authentication-through-use-public-key-infrastructure-pki","title":"User Authentication Through the Use of Public Key Infrastructure (PKI","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.0o27YRs5YVzA9rZaaCkdNAHaE3&pid=15.1","size":"700 x 460 \u00b7 gif","desc":"pki key infrastructure authentication user through certificate dimitri meacham contributed robert","filetype":"gif","width":700,"height":460,"domain":"infosecwriters.com","created_at":null,"updated_at":null,"id":1149,"keyword_id":76,"url":"https:\/\/www.manageengine.com\/products\/passwordmanagerpro\/help\/images\/smartcardauthentication.jpg","link":"http:\/\/www.manageengine.com\/products\/passwordmanagerpro\/help\/smart-card-authentication.html","title":"Smart Card Authentication","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.HOGPs5Zi7rvhI9Yri-MzsQHaFA&pid=15.1","size":"800 x 541 \u00b7 jpeg","desc":"authentication smart card process smartcard server password user access enabling web manager interface","filetype":"jpg","width":800,"height":541,"domain":"www.manageengine.com","created_at":null,"updated_at":null,"id":1150,"keyword_id":76,"url":"http:\/\/1.bp.blogspot.com\/_tebyDeNhwDs\/SlNyTZvmgEI\/AAAAAAAAABo\/nROxF19_tKk\/s400\/image005.png","link":"http:\/\/another-soa-blog.blogspot.com\/2009\/07\/v-behaviorurldefaultvml-o.html","title":"fred's integration blog","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.faPIvchYveX4yPuGjaQD2AAAAA&pid=15.1","size":"400 x 344 \u00b7 png","desc":"pki certificate fred integration usage figure","filetype":"png","width":400,"height":344,"domain":"another-soa-blog.blogspot.com","created_at":null,"updated_at":null,"id":1151,"keyword_id":76,"url":"https:\/\/doc.nexusgroup.com\/rest\/documentConversion\/latest\/conversion\/thumbnail\/24346692\/1","link":"https:\/\/doc.nexusgroup.com\/display\/PUB\/Nexus GO PKI Card layouts and technology","title":"Nexus GO PKI Card layouts and technology - - Nexus Documentation","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.4f7I2RVUwyenYuiFHnBi0gAAAA&pid=15.1","size":"243 x 310 \u00b7 jpeg","desc":"","filetype":"jpg","width":243,"height":310,"domain":"doc.nexusgroup.com","created_at":null,"updated_at":null,"id":1152,"keyword_id":76,"url":"https:\/\/www.microsec.hu\/sites\/default\/files\/e-szig_0.jpg","link":"https:\/\/www.microsec.hu\/en\/pki-blog\/personal-e-id-cards-hungary","title":"Personal e-ID cards in Hungary ,"id":1153,"keyword_id":76,"url":"http:\/\/www.hidglobal.com\/sites\/hidglobal.com\/files\/activid-usb-display-token-cap_0.png","link":"http:\/\/hidglobal.com\/products\/cards-and-credentials\/activid\/usb-tokens","title":"ActivID\u00ae ActivKey USB Tokens \u2013 Two Factor Authentication - HID Global","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.qhqQDOawGYnq2hqig-HD_AHaHa&pid=15.1","size":"800 x 800 \u00b7 png","desc":"usb hid tokens activid token pki authentication specifications overview hidglobal factor","filetype":"png","width":800,"height":800,"domain":"hidglobal.com","created_at":null,"updated_at":null,"id":1154,"keyword_id":76,"url":"https:\/\/ocio.nih.gov\/Smartcard\/PublishingImages\/LT_SCreader.jpg","link":"https:\/\/ocio.nih.gov\/Smartcard\/Pages\/PIV_cardreader.aspx","title":"HHS ID Badge Smart Card","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.SxfvS1f5TQnnfRi-QbW7qAAAAA&pid=15.1","size":"316 x 227 \u00b7 jpeg","desc":"card smart computer smartcard built reader laptop piv slot nih badge","filetype":"jpg","width":316,"height":227,"domain":"ocio.nih.gov","created_at":null,"updated_at":null, Linux Journal","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.yCP1eTnVsWIRSTx-5vJ3kgHaD8&pid=15.1","size":"516 x 275 \u00b7 jpeg","desc":"biometrics key linuxjournal pki smart cards receiver figure","filetype":"jpg","width":516,"height":275,"domain":"www.linuxjournal.com","created_at":null,"updated_at":null,"id":1156,"keyword_id":76,"url":"https:\/\/www.mysmartlogon.com\/wp\/wp-content\/uploads\/2014\/09\/logon-process.png","link":"http:\/\/www.mysmartlogon.com\/eidauthenticate\/","title":"EIDAuthenticate - Smart card authentication on stand alone computers","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.O5OaEvc6uxaNBPLXun8l_gHaFj&pid=15.1","size":"620 x 465 \u00b7 png","desc":"card smart authentication logon process computers alone stand","filetype":"png","width":620,"height":465,"domain":"www.mysmartlogon.com","created_at":null,"updated_at":null,"id":1157,"keyword_id":76,"url":"http:\/\/lmeprogramoffice.org\/PKI.jpg","link":"http:\/\/lmeprogramoffice.org\/PKIandApplicationAccess.html","title":"PKI and Application Access","thumbnail":"https:\/\/tse1.mm.bing.net\/th?id=OIP.mqqEedMdDNxOl4o7IY7VHQAAAA&pid=15.1","size":"344 x 202 \u00b7 jpeg","desc":"pki breach","filetype":"jpg","width":344,"height":202,"domain":"lmeprogramoffice.org","created_at":null,"updated_at":null,"id":1158,"keyword_id":76,"url":"http:\/\/www.certificatestemplatesfree.com\/wp-content\/uploads\/2018\/01\/certificate-hierarchy-figure-chain-LoeGdH.jpg","link":"http:\/\/www.certificatestemplatesfree.com\/certificate-hierarchy-219.html","title":"Certificate Hierarchy \u2013 certificates templates free","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.a8NfdeLLUCx26Lc-wyDs7QHaEJ&pid=15.1","size":"690 x 387 \u00b7 jpeg","desc":"certificate hierarchy chain trust root certificates path chains certification digicert order solution pki admin february january","filetype":"jpg","width":690,"height":387,"domain":"www.certificatestemplatesfree.com","created_at":null,"updated_at":null, \u03a3\u03a5\u0396\u0395\u03a5\u039e\u0399\u03a3","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.v79KApkbM4FBqQr5eY1i9AAAAA&pid=15.1","size":"324 x 374 \u00b7 jpeg","desc":"","filetype":"jpg","width":324,"height":374,"domain":"www.syzefxis.gov.gr","created_at":null,"updated_at":null,"id":1160,"keyword_id":76,"url":"https:\/\/playbooks.idmanagement.gov\/assets\/piv\/elements.png","link":"https:\/\/playbooks.idmanagement.gov\/piv\/basics\/","title":"PIV Overview","thumbnail":"https:\/\/tse4.mm.bing.net\/th?id=OIP.KqCNBDjTDsQMjPhK9P2tCAHaHW&pid=15.1","size":"1258 x 1248 \u00b7 png","desc":"piv overview","filetype":"png","width":1258,"height":1248,"domain":"playbooks.idmanagement.gov","created_at":null,"updated_at":null,"id":1161,"keyword_id":76,"url":"https:\/\/image.slidesharecdn.com\/5-160324184403\/95\/fido-pki-beyond-where-authentication-meets-identification-12-638.jpg?cb=1458845199","link":"https:\/\/www.slideshare.net\/FIDOAlliance\/fido-pki-beyond-where-authentication-meets-identification","title":"FIDO, PKI & beyond: Where Authentication Meets Identification","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.I_sqBCT4xDzE6olXVUNuXAHaFj&pid=15.1","size":"638 x 479 \u00b7 jpeg","desc":"fido pki authentication ctbc","filetype":"jpg","width":638,"height":479,"domain":"www.slideshare.net","created_at":null,"updated_at":null,"id":1162,"keyword_id":76,"url":"https:\/\/docs.centrify.com\/Content\/zint-linux-smartcd\/Images\/pkcs_gp_option.png","link":"https:\/\/docs.centrify.com\/Content\/zint-linux-smartcd\/AuthEnable.htm","title":"Enabling smart card support","thumbnail":"https:\/\/tse3.mm.bing.net\/th?id=OIP.FYTTKg9rLfBzOwPtXCraOAAAAA&pid=15.1","size":"408 x 475 \u00b7 png","desc":"pkcs smart card centrify module enabling support path complete","filetype":"png","width":408,"height":475,"domain":"docs.centrify.com","created_at":null,"updated_at":null,"id":1163,"keyword_id":76,"url":"https:\/\/doctorhoster.com\/blog\/wp-content\/uploads\/2021\/05\/image-10-721x420.png","link":"https:\/\/doctorhoster.com\/blog\/how-to-use-pknic-prepaid-card\/","title":"How to use PKNIC Prepaid Card? ,"id":1164,"keyword_id":76,"url":"https:\/\/www.sparklabs.com\/support\/kb\/article\/using-tokens-smartcards-pkcs-11\/pkcs11-detect-macos","link":"https:\/\/www.sparklabs.com\/support\/kb\/article\/using-tokens-smartcards-pkcs-11\/","title":"Using Tokens\/Smartcards (PKCS#11) - SparkLabs","thumbnail":"https:\/\/tse2.mm.bing.net\/th?id=OIP.oBK5Z3LYLixblI0NApHFugHaDs&pid=15.1","size":"1220 x 608 \u00b7 png","desc":"pkcs using smartcards sparklabs tokens","filetype":"png","width":1220,"height":608,"domain":"www.sparklabs.com","created_at":null,"updated_at":null] this site you are coming to the right page. Contains many images about pki card Pki breach. Don't forget to bookmark this page for future reference or share to facebook / twitter if you like this page.
Comments
Post a Comment